Guest Opinion: How Modern Warfare Can Target Vulnerable IIoT Devices
Security Industry Association
OCTOBER 23, 2023
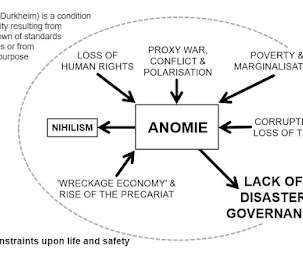
i-PRO Americas’ Will Knehr shares tips for securing industrial Internet of Things devices. Hacktivist groups have specifically targeted SCADA, ICS systems and other potentially vulnerable systems to cause disruptions to critical infrastructure.
















































Let's personalize your content