Disaster Recovery (DR) Architecture on AWS, Part IV: Multi-site Active/Active
AWS Disaster Recovery
JUNE 23, 2021
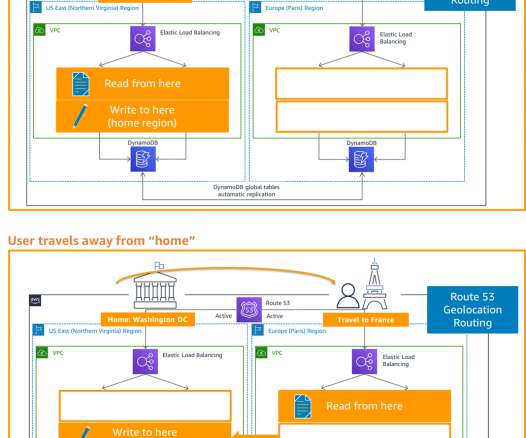
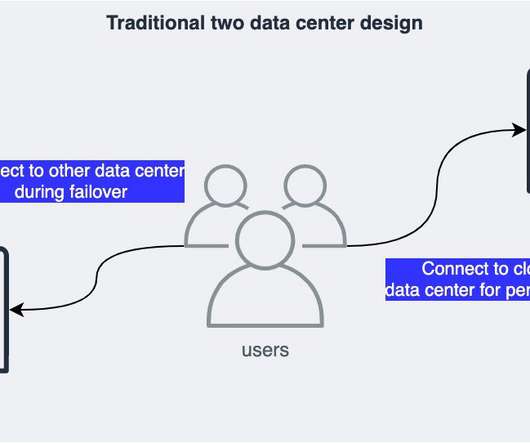
My subsequent posts shared details on the backup and restore , pilot light, and warm standby active/passive strategies. In this post, you’ll learn how to implement an active/active strategy to run your workload and serve requests in two or more distinct sites. DR strategies: Multi-site active/active. DR strategies.

















































Let's personalize your content