Changes Continue in Cyber Insurance
Pure Storage
MARCH 6, 2024
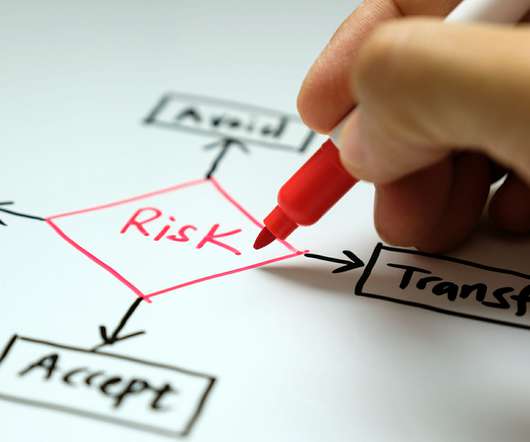
Changes Continue in Cyber Insurance by Pure Storage Blog An ounce of prevention is worth a pound of cure certainly applies to physical health. Prevention begins with having a robust cybersecurity plan in place, along with sufficient insurance to manage risk. In 2010, cyber insurance premiums totaled a mere $600,000.

















































Let's personalize your content