Navigating Resilience: How to Create a BCM Roadmap
MHA Consulting
SEPTEMBER 7, 2023
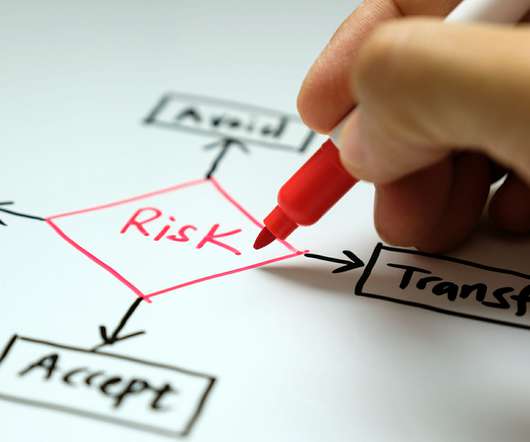
Related on MHA Consulting: Get Out the Map: Why Your BCM Program Needs a Roadmap The Power of the Map At MHA, we believe strongly in the value of roadmaps. Decide whether you will seek help from a consultant and/or utilize one of the commercially available software tools. We think they’re essential.

















































Let's personalize your content