APAC Retrospective: Learnings from a Year of Tech Outages, Restore: Repair vs Root Cause by David Ridge
PagerDuty
JANUARY 22, 2024
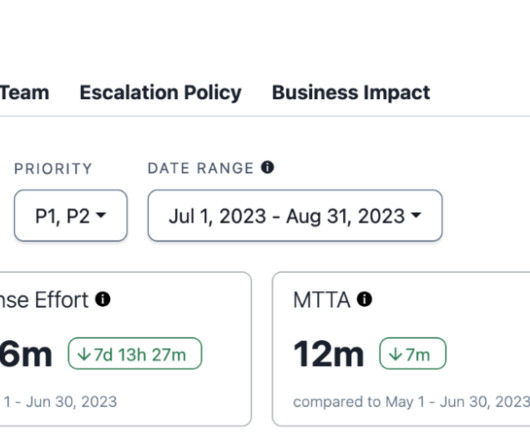
Faced with a range of disruptions from major technical glitches to cloud service failures and cybersecurity risks, today’s businesses must be strategically poised for incident response. When an IT outage strikes, the primary concern is the rapid restoration of services.






































Let's personalize your content