Covid-19: Elements of a Scenario
Emergency Planning
MARCH 11, 2020
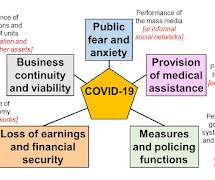
It is now more than ten years since there was a general push to induce countries to plan for pandemics (WHO 2005). US Homeland Security Council 2005, UK Government 2008), while in others it did not. That was at a time when an influenza pandemic with devastating consequences was greatly feared.












































Let's personalize your content