Ransomware and Healthcare Payers: What Can You Do to Protect Yourself
Pure Storage
APRIL 17, 2024
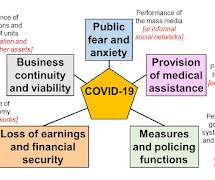
Unfortunately, even the most sophisticated organizations that deploy comprehensive hardware and software solutions are vulnerable. If a ransomware event happens, payer organizations can’t process authorizations, check eligibility for benefits, and often cannot connect with their providers or members.



































Let's personalize your content