Field Notes: Protecting Domain-Joined Workloads with CloudEndure Disaster Recovery
AWS Disaster Recovery
FEBRUARY 18, 2021
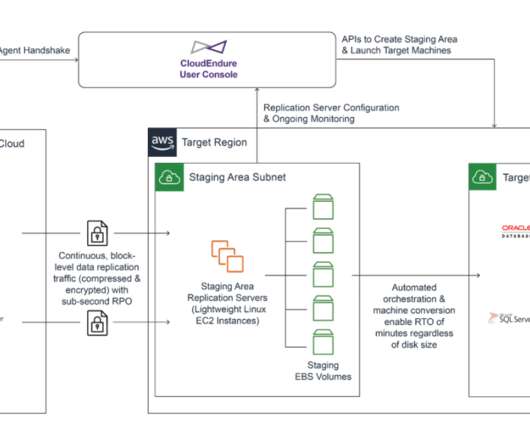
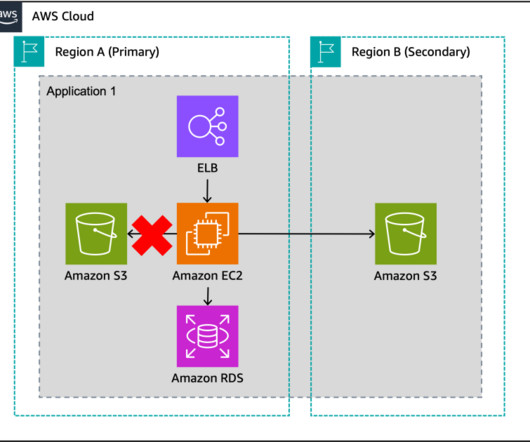
Co-authored by Daniel Covey, Solutions Architect, at CloudEndure, an AWS Company and Luis Molina, Senior Cloud Architect at AWS. When designing a Disaster Recovery plan, one of the main questions we are asked is how Microsoft Active Directory will be handled during a test or failover scenario. Overview of architecture.










































Let's personalize your content