Security Industry Association Announces 2024 Winners of the SIA Women in Biometrics Awards
Security Industry Association
MAY 7, 2024
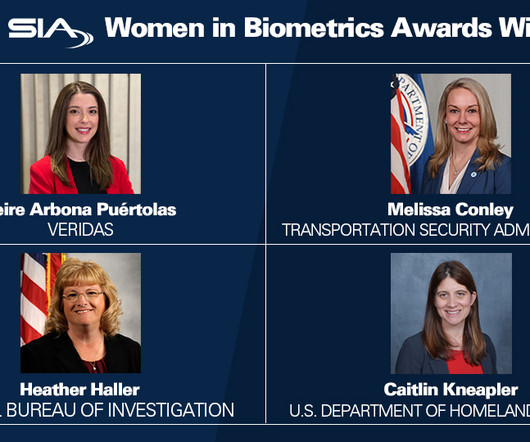
Leire Arbona Puértolas, Melissa Conley, Heather Haller and Caitlin Kneapler will be honored for their leadership and contributions in biometrics and security at the 2024 SIA GovSummit. Department of Homeland Security (DHS) and TSA strategies and priorities. SILVER SPRING, Md. –

















Let's personalize your content