The Future of Business Continuity: Innovations and Emerging Technologies
Erwood Group
FEBRUARY 4, 2024
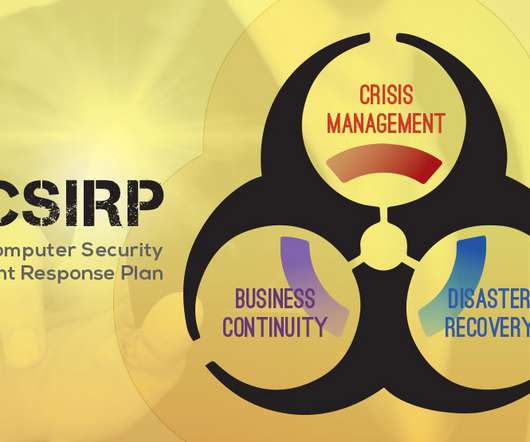
The Future of Business Continuity The Future of Business Continuity: Innovations and Emerging Technologies In an era of rapid technological advancement, the landscape of business continuity is evolving, embracing innovations and emerging technologies to enhance resilience.


















































Let's personalize your content