The Top 8 Risk Mitigation Controls, in Order
MHA Consulting
MAY 4, 2023
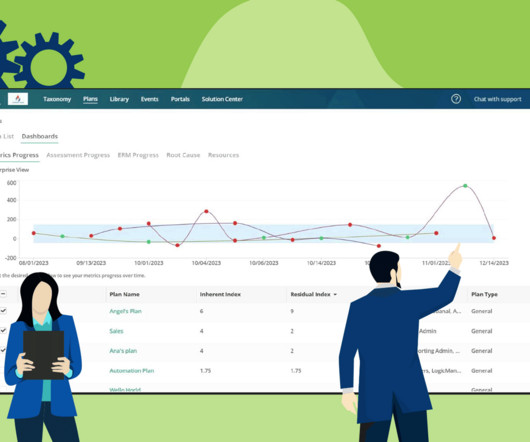
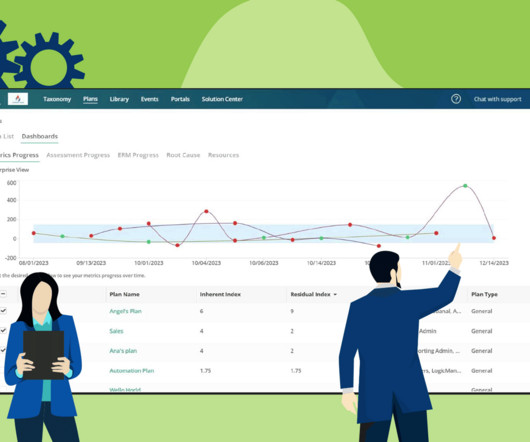
Risk mitigation controls are the measures we take to reduce the risks our organizations face in carrying out their operations. Related on MHA Consulting: The Ultimate Guide to Residual Risk Risk Mitigation Controls Explained Business continuity is all about reducing risk. You can see why risk mitigation controls are important.












































Let's personalize your content