Covid-19: Elements of a Scenario
Emergency Planning
MARCH 11, 2020
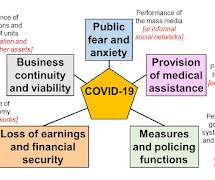
It is now more than ten years since there was a general push to induce countries to plan for pandemics (WHO 2005). About the same time, 2007, Dr Michael Leavitt of the US Department of Health and Human Services wrote: "We don't know when a pandemic will arrive. Major epidemics and pandemics (what is the difference?)






























Let's personalize your content