Customer Value Story: How to Know What You Don’t Know
LogisManager
NOVEMBER 17, 2021
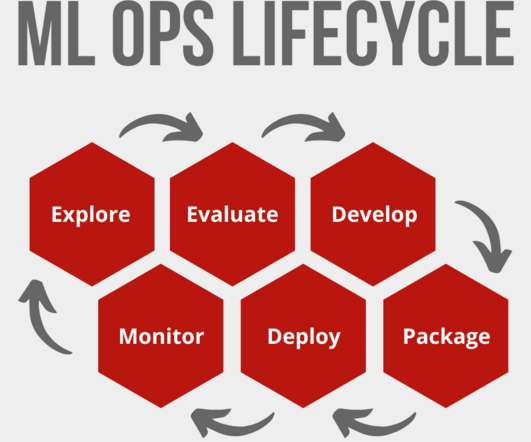
This series of blog posts shares our best customer value stories to help other businesses find similar successes. This AI-powered feature was a good fit for this client as it positioned them to significantly streamline their due diligence process and keep an audit trail of their work. Introduction.







































Let's personalize your content