VMware Explore Barcelona 2023 Recap
Zerto
NOVEMBER 13, 2023
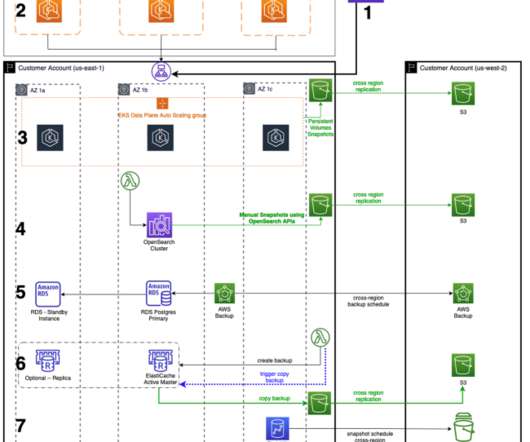
Though ransomware has dominated conversations in the data protection sphere for quite some time, stories of recent outages due to this threat still circulate. The conversation delved into the technical design aspects of the vault, its architecture, and the rationale behind crucial decisions.


































Let's personalize your content