Do You Need Cybersecurity Insurance?
LAN Infotech
JANUARY 18, 2022
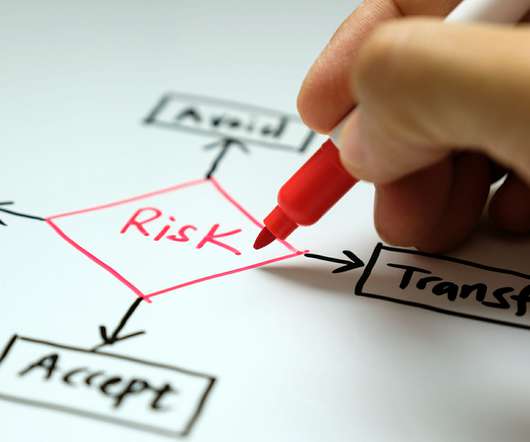
Do You Need Cybersecurity Insurance and Do You Qualify for It? This means businesses will be more vulnerable, especially those who do not take critical measures to mitigate cybercrimes. But the question is, do you qualify for cybersecurity insurance? What is Cybersecurity Insurance?

















































Let's personalize your content