Expert Reveals 3 High Availability for SQL Server in AWS Options
Solutions Review
MARCH 30, 2023
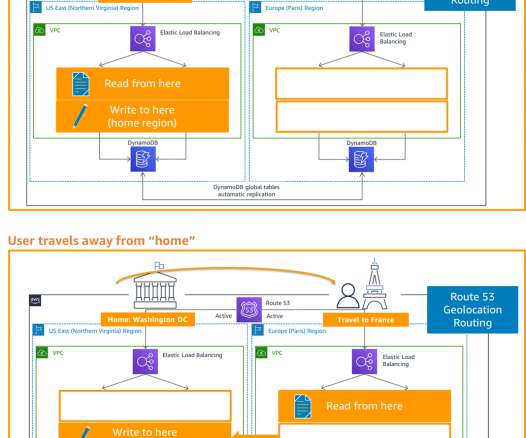
If you want true high availability – meaning that your SQL Server database will be accessible 99.99 The PaaS offering — Amazon RDS – falls out of the running because its service level agreement (SLA) only guarantees an availability level of 99.95 Will you use SQL Server’s built-in Availability Groups (AG) functionality?














































Let's personalize your content