Strategic Risk Management
LogisManager
DECEMBER 19, 2023
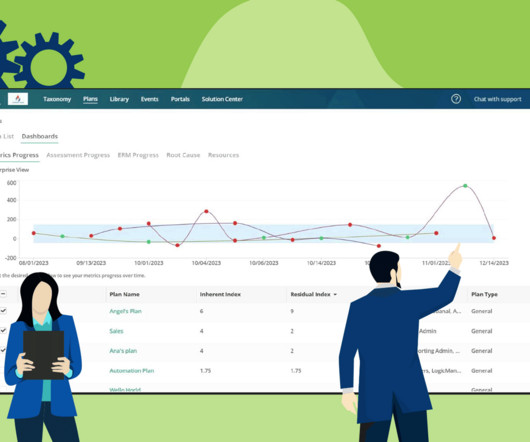
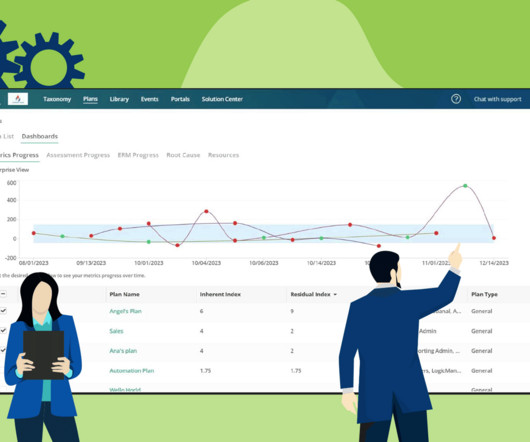
Strategic Risk Management Last Updated: December 19, 2023 Strategic Risk Management (SRM) is integral to navigating the complexities of today’s business landscape and securing long-term objectives. What Is Strategic Risk Management? How Do Strategic Risks Differ From Tactical Risks?

















































Let's personalize your content