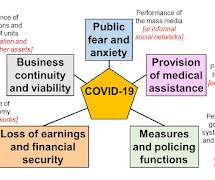
Covid-19: Elements of a Scenario
Emergency Planning
MARCH 11, 2020
In the wake of the WHO report, Professor Ziad Abdeen of the Palestinian Health Authority said about pandemics: "My task is to tell you things you don't want to know, and ask you to spend money you haven't got on something you don't think will happen."





















Let's personalize your content