How to Offload Your Risk to a Third Party
MHA Consulting
FEBRUARY 9, 2023
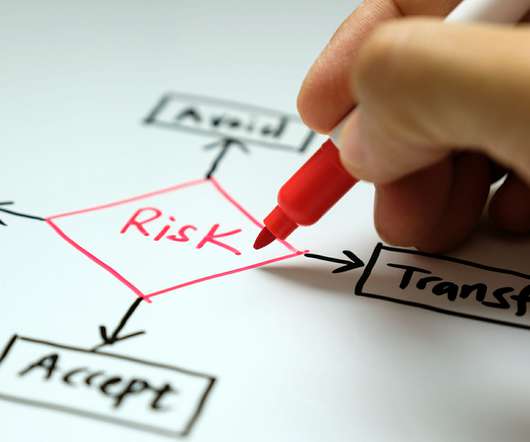
Try a Dose of Risk Management Wise organizations determine how much risk they will accept then make conscious efforts to bring their risk down below that threshold. Risk avoidance: Altering organizational behavior to eliminate a given risk. Related on MHA Consulting: Global Turmoil Making You Ill?



















Let's personalize your content