Disaster Response and Equity: Reflecting on the Racial Disparities in Texas Power Outages
National Center for Disaster Prepardness
MARCH 27, 2023
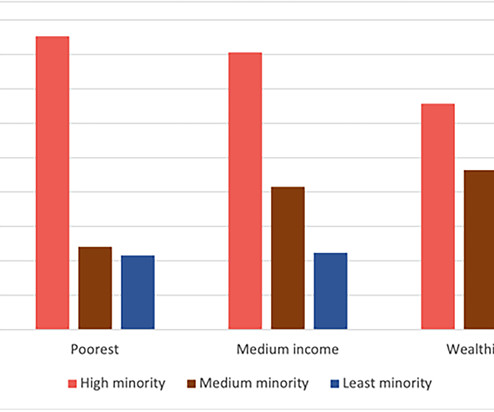
This February marked two years since Texans were hit with widespread power outages during the deep freeze of 2021. The state’s energy supply chain was unable to withstand the sustained low temperatures, as generation resources were strained due to cold weather tripping units, natural gas supply curtailments, and wind power generation outages.

























Let's personalize your content