How to Offload Your Risk to a Third Party
MHA Consulting
FEBRUARY 9, 2023
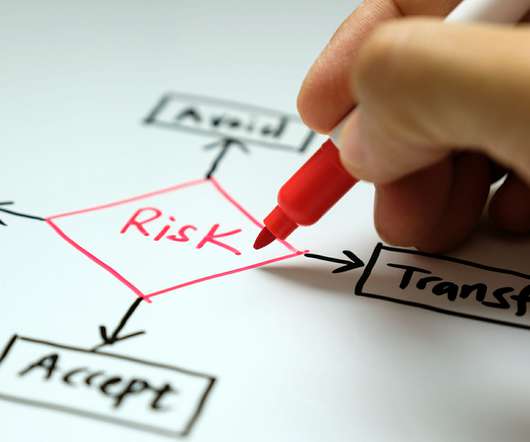
There are four main strategies for mitigating risk : · Risk acceptance: Making a conscious decision to remain vulnerable to a potential harm, usually based on a cost-benefit analysis. Companies often hire third parties to take on activities that are outside their core competencies, freeing them to do what they do best.



















Let's personalize your content