Unlocking the Value of your Runbook Automation Value Metrics with Snowflake, Jupyter Notebooks, and Python by Justyn Roberts
PagerDuty
JANUARY 5, 2024
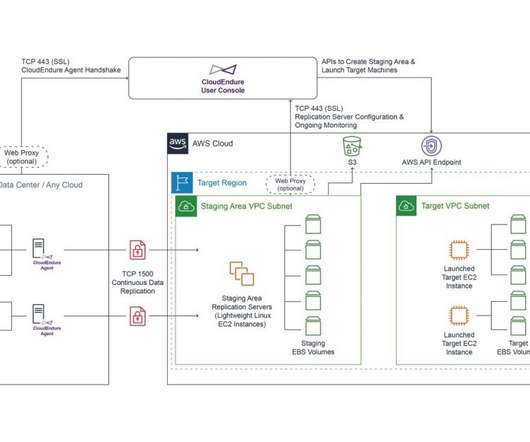
Understanding the value derived from automated jobs and return on investment (ROI) from these automated processes is a critical metric for value realization, be it in terms of time saved, errors avoided, risk mitigation, number of executions, etc. Each individual job may have its own metric or metrics. 1h, 24h,1d,14d).

















Let's personalize your content