Don’t be left in the dark: Here’s how to create a business continuity plan that works
Online Computers
MARCH 10, 2023
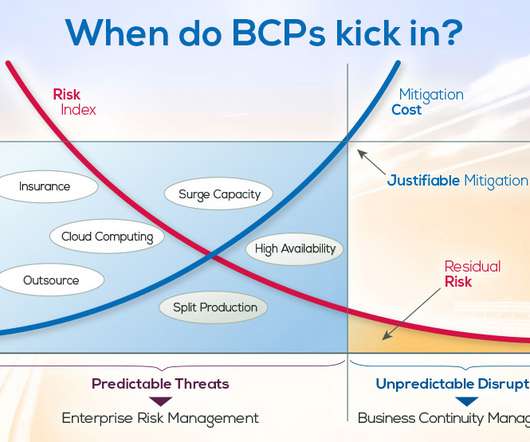
A business continuity plan (BCP) is a vital document that outlines the procedures and strategies an organization must follow to be able to continue operating in the event of an emergency or a disaster. Assess your company's risks and vulnerabilities Identify the potential risks and threats that your business may face.






















Let's personalize your content