The Importance of Risk Analytics
LogisManager
DECEMBER 5, 2023
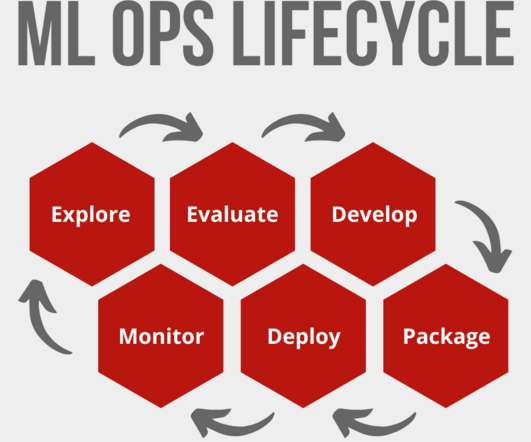
The RMM not only assesses ERM program maturity but also highlights gaps in risk coverage, providing actionable insights and benchmarking against industry standards. The Internal Auditor’s Guide The Audit guide is a valuable resource for your risk and audit teams to work together to make sure you are meeting the obligations of the board.


























Let's personalize your content