Five Strategies for Achieving Application High Availability
Solutions Review
JANUARY 19, 2024
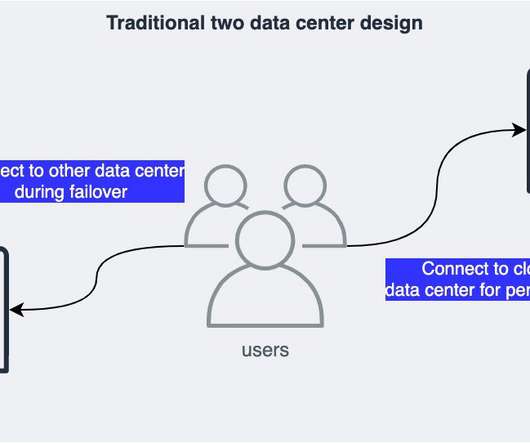
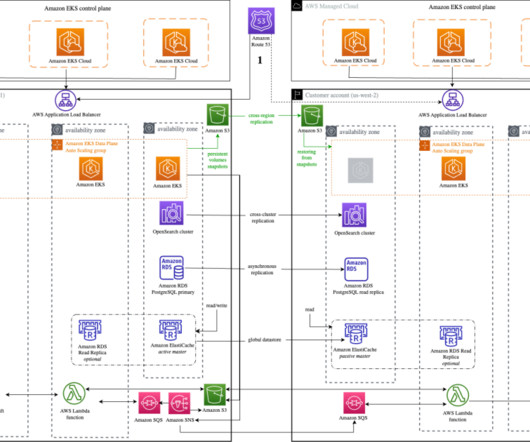
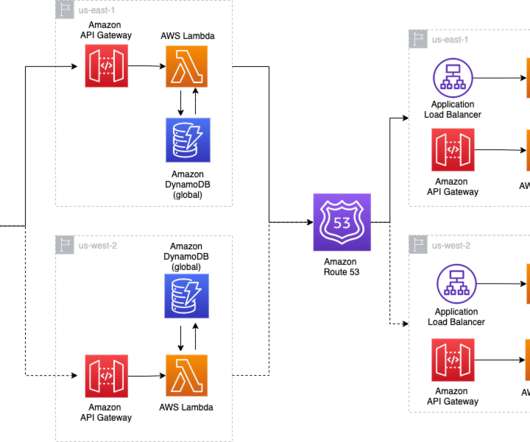
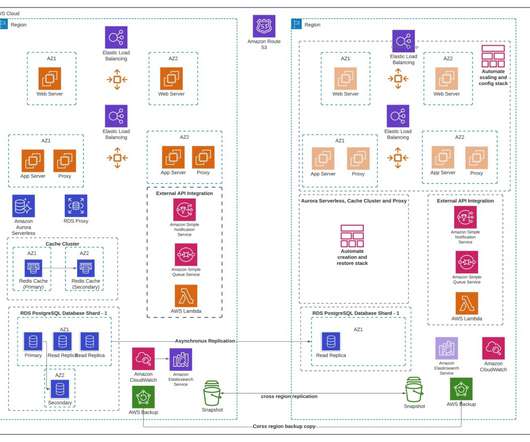
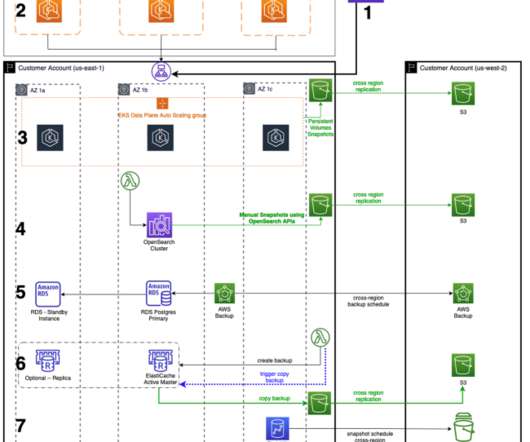
In this feature, SIOS Technology ‘s Todd Doane offers five strategies for achieving application high availability. Business-critical applications, such as SAP, S/4 HANA, SQL Server, and MaxDB, serve as the backbone of many organizations. The company relied on securities trading applications based on Oracle Database.








































Let's personalize your content