Disasters: Knowledge and Information in the New Age of Anomie
Emergency Planning
JULY 29, 2019
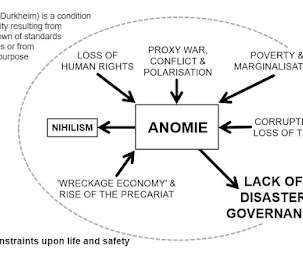
Something similar has happened with the Internet and social media. Early views of the Internet and disasters (e.g. The result is a communication process which has been termed chronic contagion (Pomerantsev 2019). Authoritarianism and the Internet. Internet and emergency management: prospects for the future.


















Let's personalize your content