Scary DR Stories 2023 Recap
Zerto
NOVEMBER 6, 2023
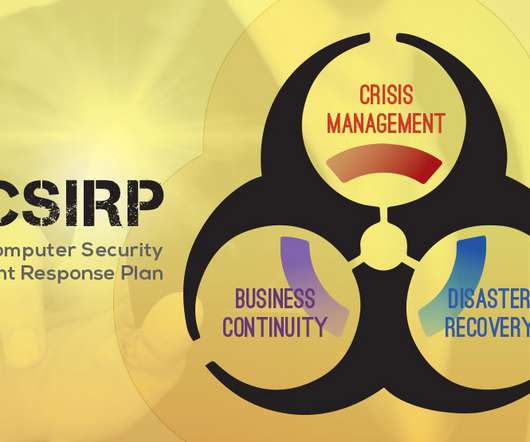
This year we had three spine-tingling tales that covered everything from hardware failures and human errors to ominous outages, monstrous migrations, and a blindsiding bioterrorism attack! The near-synchronous replication and granular journaling technology detect data encryption. These bad actors even offer ransomware as a service now!


























Let's personalize your content