How to Offload Your Risk to a Third Party
MHA Consulting
FEBRUARY 9, 2023
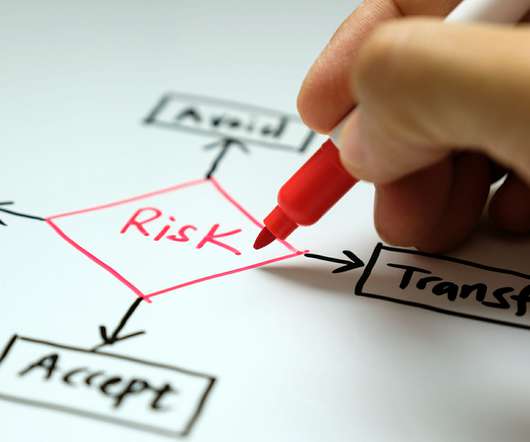
Risk transference is one of the four main strategies organizations can use to mitigate risk. Related on MHA Consulting: Global Turmoil Making You Ill? There are four main strategies for mitigating risk : · Risk acceptance: Making a conscious decision to remain vulnerable to a potential harm, usually based on a cost-benefit analysis.












Let's personalize your content