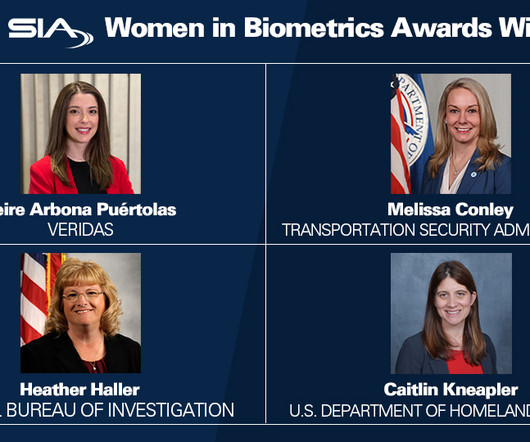
Security Industry Association Announces 2024 Winners of the SIA Women in Biometrics Awards
Security Industry Association
MAY 7, 2024
She works with a team of capability managers to integrate all materiel and non-materiel capabilities into the security architecture to ensure a cohesive set of innovative security solutions to meet the challenges of today and tomorrow. Department of Homeland Security (DHS) and TSA strategies and priorities.

















Let's personalize your content