Empowering Strategic Decision-Making with Real-Time Risk Dashboards
LogisManager
DECEMBER 12, 2023
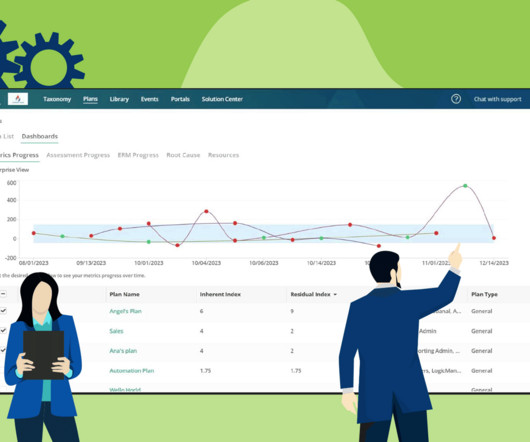
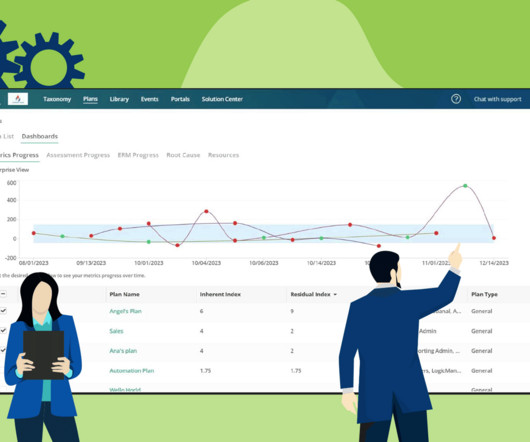
Empowering Strategic Decision-Making with Real-Time Risk Dashboards Published: December 12, 2023 In LogicManager’s latest product update release, powerful new in-app visualizations enable real-time data analysis, fostering informed decision-making and proactive risk strategies for strong corporate governance.







































Let's personalize your content