Cyber Recovery vs. Disaster Recovery
Pure Storage
JULY 18, 2023
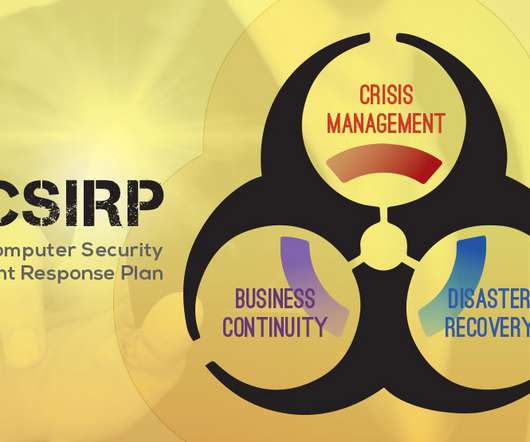
Cyber Recovery vs. Disaster Recovery by Pure Storage Blog Data infrastructures aren’t just built for storage, performance, and scale—they’re designed for resilience. Two key areas of concern include disaster recovery in general, and, more specifically, cyber recovery.



















Let's personalize your content