World Backup Day: Four Data Protection Best Practices to Know
Pure Storage
MARCH 29, 2024
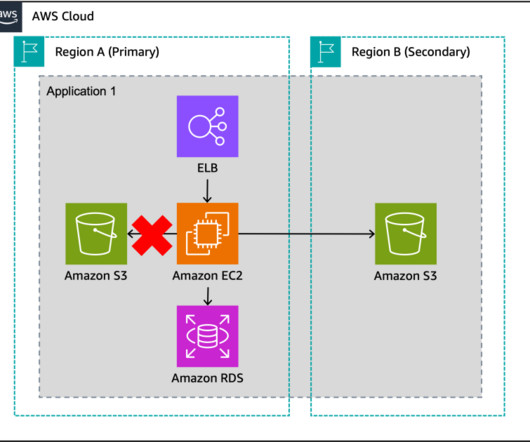
World Backup Day: Four Data Protection Best Practices to Know by Pure Storage Blog This article originally appeared on SolutionsReview.com. It has been republished with permission from the author. Tiered backup architectures use different logical and geographic locations to meet diverse backup and recovery needs.





















Let's personalize your content