How to Protect Your Database with Zerto
Zerto
JANUARY 24, 2023
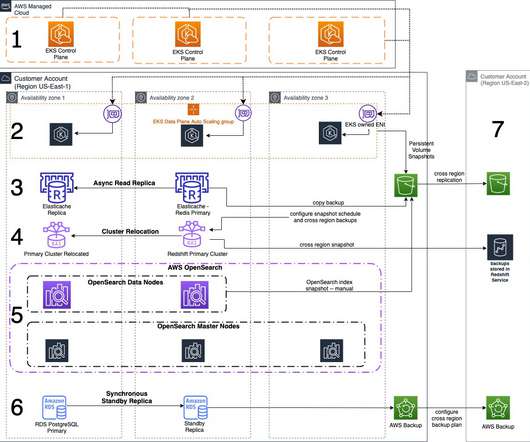
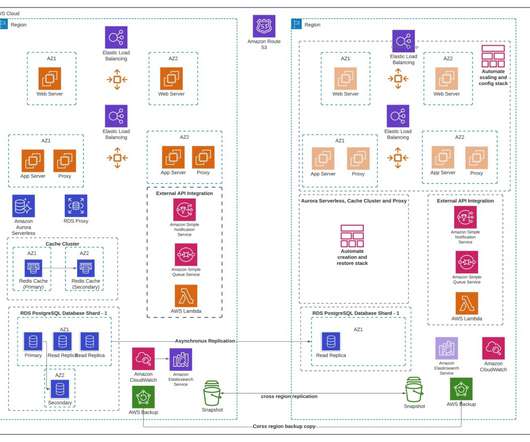
Database contents change depending on the applications they serve, and they need to be protected alongside other application components. These databases leverage a Structured Query Language (SQL) in order to organize, manage, and relate with the information stored.





































Let's personalize your content