Remember: People Are Not Paying Attention to the Weather
Disaster Zone
OCTOBER 3, 2023
New York City is a great example of that.

Disaster Zone
OCTOBER 3, 2023
New York City is a great example of that.

Recovery Diva
OCTOBER 3, 2023
From Inside Climate News: For Sanibel, the Recovery from Hurricane Ian Will Be Years in the Making. Thousands of residents of this barrier island remain displaced a year after the costliest hurricane in state history.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Zerto
OCTOBER 3, 2023
In today’s digital age, the education sector faces a growing threat: ransomware. During a ransomware attack, malicious software encrypts a school’s data, rendering it inaccessible until a ransom is paid. Ransomware can disrupt classes, compromise sensitive student and staff information, and damage your finances and reputation. A recent article on NewsNationNow, “Hackers Target Schools in Rampant Ransomware Attacks,” sheds light on the alarming surge of cyberattacks on educational institutions.

Disaster Zone
OCTOBER 3, 2023
Thinking through how to warn people traumatized from past storms.

Speaker: Tim Buteyn, President of ThinkingKap Learning Solutions
💢 Do you find yourself stuck in never-ending review cycles? Are you wondering if your Subject Matter Expert actually got that last review request? Are you having trouble trying to decipher impractical or conflicting feedback? 💢 If any of these scenarios sounds familiar, you may benefit from a crash course on managing SME relationships!

CCEM Strategies
OCTOBER 3, 2023
After almost 30 years[1] since the last substantial update (1993) to B.C.’s current emergency management legislation (the Emergency Program Act ), the B.C. NDP introduced new legislation for a 1st reading on October 3rd, 2023, the first day of the fall legislative session. This comes as the Province of B.C. continues to respond to and begins recovery from the most destructive and most expensive[2] wildfire season in provincial history.
Continuity Professional Pulse brings together the best content for business continuity professionals from the widest variety of industry thought leaders.

The Rand Blog
OCTOBER 3, 2023
A proper understanding of the threat Russia poses must begin with an accurate appraisal of Russian power. Putin might harbor fantasies of world conquest. But his military cannot even fully conquer any of the four Ukrainian provinces he claims to have annexed last year. Ultimately, those are the constraints that should bound the debate about the extent of the threat.
Acronis
OCTOBER 3, 2023
Accelerate your learning curve with our specialized courses tailored for quick and effective results. Regardless of your experience level, we provide training to help you create valuable and marketable integrations. In this section, we emphasize Offering Items and Applications Management, equipping you with essential skills in integration development.

Pure Storage
OCTOBER 3, 2023
Looking for Simplified Inventory Management for Your Pure Portfolio? Pure1 Assets Has Got You Covered by Pure Storage Blog Managed service providers, asset management teams, and partners will be delighted to know that Pure1 ® provides a centralized portal for asset management, auditing, and tracking the evolution over time for all Pure assets. The Assets portal is divided into three pages: Asset Management Appliance Genealogy Subscription Genealogy Figure 1: Asset Management page in Pure1.

Speaker: Tim Buteyn
Let's set the scene: you’ve identified a critical performance gap in your organization and need to close that gap. A colleague suggests training, but you suspect there’s something going on that training can’t address. How can you determine if training is the right solution before you commit your budget and resources to a new training program? In this webinar, you will learn how to determine if training is the right solution using the Behavior Engineering Model.
Acronis
OCTOBER 3, 2023
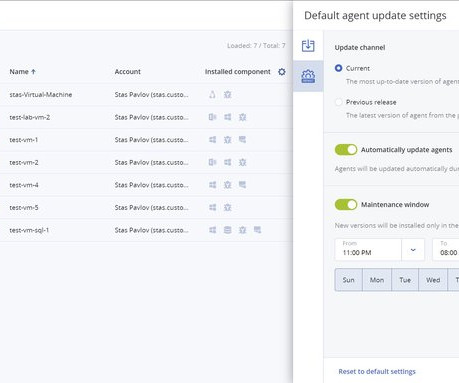
Discover the latest release of Acronis Cyber Cloud with the highly demanded feature of Agent auto-updating. Take advantage of the corresponding public API to control updates. Easily customize automatic update settings on a data center level and tailor them for your company, unit, or individual devices.
Acronis
OCTOBER 3, 2023
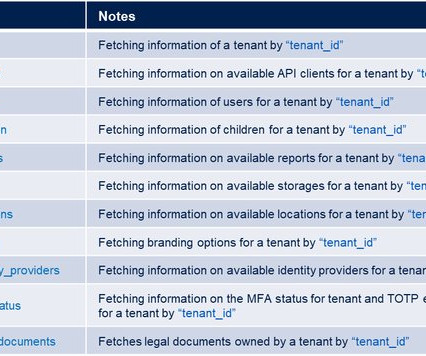
Fast-track your progress with our carefully crafted courses. Whether you're a seasoned developer or new to the field, we offer training to enhance your ability to create valuable and marketable integrations. In this section, we put the spotlight on Authorization and Tenants Management, empowering you to master these crucial aspects of integration development.
Acronis
OCTOBER 3, 2023
Simplify software installation automation in IaaS environments to enhance customer services. Acronis Cyber Protect offers integrated backup, AI-based anti-malware, and endpoint protection management.

Acronis
OCTOBER 3, 2023
Automate provisioning to reduce costs and standardize customer provisioning. Take it further by automating protection management and proactive monitoring. Acronis Cyber Platform API offers comprehensive functionality for building sophisticated monitoring systems. Overcome implementation challenges with our guidance.

Speaker: Tim Buteyn, President of ThinkingKap Learning Solutions
We’ve all been there. You’ve been given a pile of dry content and asked to create a compelling eLearning course. You’re determined to create something more engaging than the same old course that learners quickly click through, but how do you take this “boring” content and create something relevant and engaging? Many instructional designers will say, “Boring in means boring out.
Acronis
OCTOBER 3, 2023
In the era of the API economy, testing API compatibility with solution architecture and approach is essential. Explore the power of prototyping with Postman, a widely used tool. This document focuses on leveraging Postman for API prototyping.

Acronis
OCTOBER 3, 2023
Discover the benefits of test automation in this insightful article by a1qa, a leading software testing company. Learn how to kickstart the adoption of test automation, its role in continuous and shift-left testing, and the tangible advantages it brings to software development.
Acronis
OCTOBER 3, 2023
Simplify software installation automation in IaaS environments to enhance customer services. Explore the seamless integration of backup, AI-based anti-malware, and endpoint protection management in Acronis Cyber Protect. This article provides a step-by-step guide on automating the installation of the Acronis Cyber Protect Agent.

Acronis
OCTOBER 3, 2023
Unlock greater operational efficiency for MSPs with the seamless integration of Acronis and Atera solutions. Spend more time engaging with clients and less on deployments and service desk tickets. Discover the advanced monitoring capabilities enabled by Acronis Cyber Platform API in this comprehensive tutorial, supporting a range of use cases.

Speaker: Chester Santos – Author, International Keynote Speaker, Executive Coach, Corporate Trainer, Memory Expert, U.S. Memory Champion
In October, scientists discovered that 75% of patients who experienced brain fog had a lower quality of life at work than those who did not. At best, brain fog makes you slower and less efficient. At worst, your performance and cognitive functions are impaired, resulting in memory, management, and task completion problems. In this entertaining and interactive presentation, Chester Santos, "The International Man of Memory," will assist you in developing life-changing skills that will greatly enha
Acronis
OCTOBER 3, 2023
Transitioning to a microservice architecture necessitates reevaluating various aspects of the software component life cycle, including development, testing, support, and design. In this post, discover the proven practices employed by Acronis architects to develop top-notch API components. From objective setting to solution analysis, gain insights into their approach.

Acronis
OCTOBER 3, 2023
Unlock the power of Bash for efficient management tasks, especially for Linux workloads. Explore in-depth guidance on leveraging Bash to solve common tasks using the Acronis Cyber Platform API. Discover the seamless integration of Bash and Acronis Cyber Platform API for streamlined management workflows.
Acronis
OCTOBER 3, 2023
Harness the power of PowerShell, a versatile scripting tool, for efficient management tasks, especially in Microsoft infrastructure. With PowerShell Core, it extends to Linux workloads as well. Dive deep into leveraging PowerShell to solve common tasks using the Acronis Cyber Platform API. Explore the seamless integration of PowerShell and Acronis Cyber Platform API for enhanced management capabilities.

Acronis
OCTOBER 3, 2023
Pax8, the leading cloud distribution provider for the IT channel, addresses the evolving needs of the distribution ecosystem and the rise of cloud delivery models. With a focus on simplifying cloud buying, Pax8 empowers the IT channel through comprehensive services including billing, provisioning, automation, PSA integrations, and pre-and-post sales support.
Acronis
OCTOBER 3, 2023
In the dynamic world of microservices, change is constant. Components can be rewritten in different languages, frameworks, or architectures. However, contracts remain constant, defining the interaction of microservices regardless of internal changes.

Acronis
OCTOBER 3, 2023
Discover our Acronis Cyber Platform API, now open for partners and developers. Access clear code examples for real-life development tasks, including a fully functional Acronis Cyber Cloud integration for WHMCS (PHP) and base API usage examples in Python. Evaluate our API capabilities with these examples as your starting point.

Acronis
OCTOBER 3, 2023
Discover the Acronis Cyber Cloud WHMCS provisioning module, a fully functional integration available on the WHMCS Marketplace. This PHP-based module showcases Acronis Cyber Platform API usage, serving as a valuable quick start resource for building custom WHMCS modules. Reuse or modify the code under the MIT license to meet your specific needs.

Acronis
OCTOBER 3, 2023
Level up your skills with our courses designed for a quick start. Whether you're a seasoned developer or just starting out, we offer training to develop valuable and marketable integrations. In this section, we dive into Users Management, empowering you to master this key aspect of integration development.

Acronis
OCTOBER 3, 2023
Accelerate your learning journey with our comprehensive courses designed for developers of all levels. Develop high-quality, marketable integrations with ease, regardless of your experience level. In this section, we delve into usage reporting, locations, and infrastructure information for advanced skills.
Acronis
OCTOBER 3, 2023
Unlock operational efficiency for MSPs with Acronis Cyber Platform API. Free up time from deployments and service desk tickets to focus on client engagement and growth.

Acronis
OCTOBER 3, 2023
Customize Acronis Cyber Agent installation on Windows using command line parameters. Discover common customization scenarios for Windows systems in this guide.

Acronis
OCTOBER 3, 2023
Customize Acronis Cyber Agent installation on Linux using command line parameters. Explore common customization scenarios for Linux systems in this guide.
Let's personalize your content