The Industrial Revolution v4.1: with increased opportunity comes increased vulnerability
SRM
JULY 3, 2018
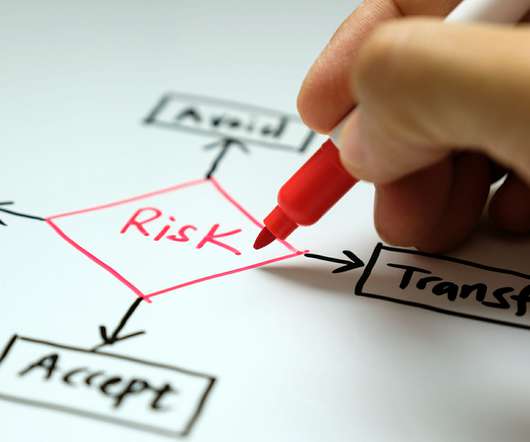
also brings an increased level of vulnerability. Disaster Recovery : taking a strategic approach to managing staff in the event of a successful attack, minimising damage to brand reputation and safeguarding the interests of key stakeholders; 3. Yet the Industrial Revolution v4.1 Penetration testing: man vs machine.
















Let's personalize your content