Five Reasons to Consider Upgrading to a Modern, Open-Architecture Access Control System
Security Industry Association
OCTOBER 18, 2022
Sebastiaan van Ineveld, product marketing manager, access control at Genetec, leads the product marketing team for access control, driving strategic marketing initiatives and go-to-market strategies. The best way to minimize costs and streamline the transition is to select an open-architecture solution for access control.



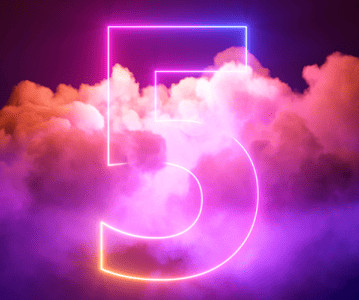




















Let's personalize your content