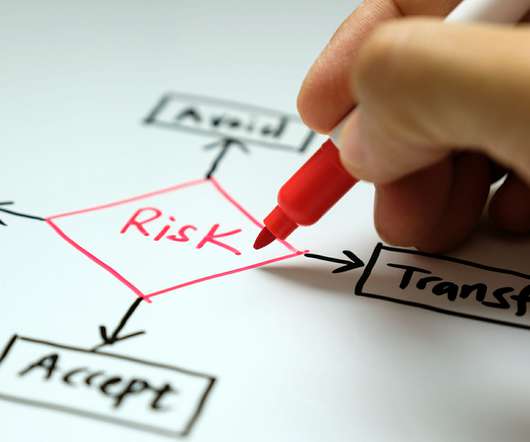
How to Offload Your Risk to a Third Party
MHA Consulting
FEBRUARY 9, 2023
These definitions are taken from our recent free ebook, Strong Language: The MHA Guide to Essential Business Continuity Terminology. There’s been a tremendous increase in outsourcing over the past several years. One function that is frequently performed by third parties is physical security. 2) Is the vendor resilient?








Let's personalize your content