Why SREs Need DR Now
Zerto
MARCH 15, 2023
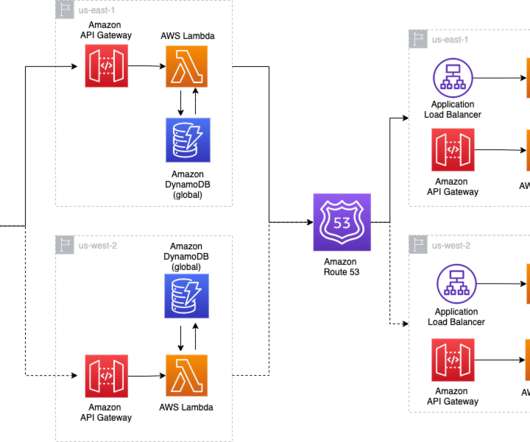
SREs and DR DR refers to the processes, procedures, and technologies used to prepare for and recover from natural or man-made disasters that threaten the availability of critical systems. DR tries to minimize the impact a disaster has on applications, restoring them to a usable state as quickly as possible.













Let's personalize your content