Risk Management as a Career: A Guide for BCM Professionals
MHA Consulting
AUGUST 24, 2023
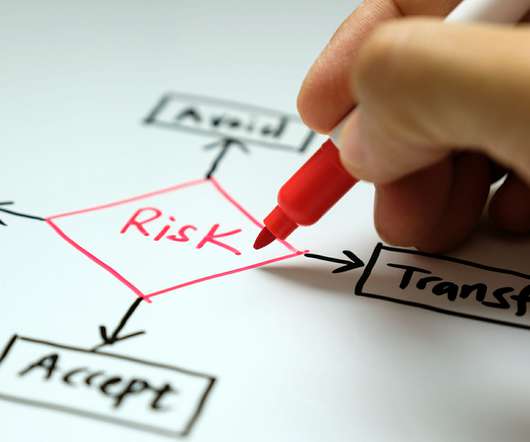
A risk manager should possess deep industry knowledge and a solid understanding of what is critical and what’s not. Good, foundational knowledge of technology. The person doesn’t have to be a tech guru, but they do need an understanding of the core components of technology and how they work. Knowledge of how to mitigate risks.














Let's personalize your content