How to Offload Your Risk to a Third Party
MHA Consulting
FEBRUARY 9, 2023
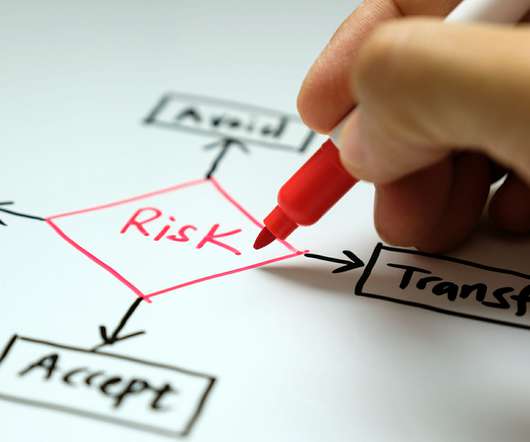
Incorporates a combination of the strategies of risk avoidance and risk acceptance. Risk transfer: Passing risk on to another organization, such as by hiring a third-party vendor to perform the associated function. You still need to have a program to ensure the continuity of your business.












Let's personalize your content