Thinking Forward: IT Governance & Cybersecurity for 2024 & Beyond
LogisManager
JANUARY 22, 2024
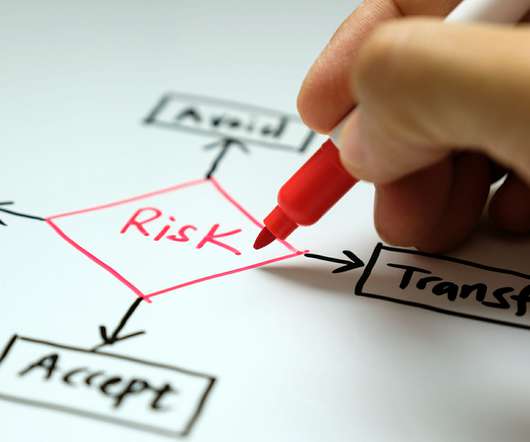
Successful leaders in the IT Governance space will proactively identify and mitigate threats before they can be exploited. Additionally, a keen understanding of your current IT Risk Maturity will be crucial in moving from a reactive approach to a proactive one.












Let's personalize your content