Creating an organizational multi-Region failover strategy
AWS Disaster Recovery
MAY 8, 2024
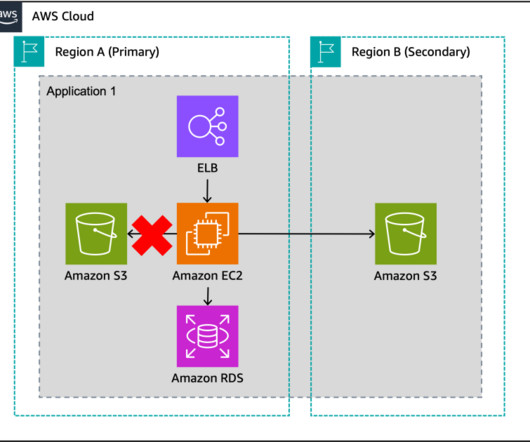
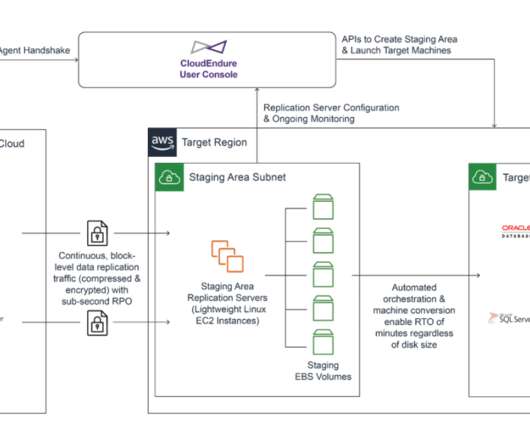
However, applications typically don’t operate in isolation; consider both the components you will use and their dependencies as part of your failover strategy. Because of this, you should develop an organizational multi-Region failover strategy that provides the necessary coordination and consistency to make your approach successful.




















Let's personalize your content