Implementing Multi-Region Disaster Recovery Using Event-Driven Architecture
AWS Disaster Recovery
JULY 27, 2021
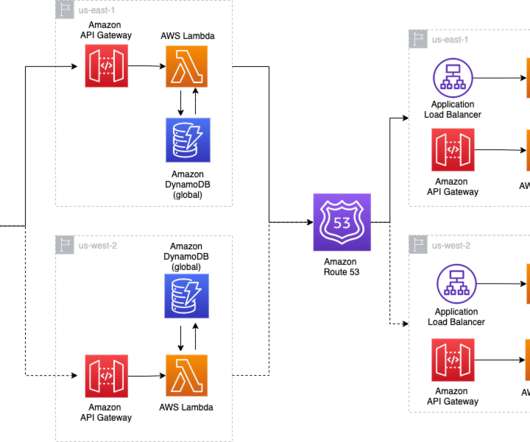
This makes your infrastructure more resilient and highly available and allows business continuity with minimal impact on production workloads. However, they will run the same version of your application for consistency and availability in event of a failure. After that, the same stack is copied to the secondary Region.











Let's personalize your content