Creating an organizational multi-Region failover strategy
AWS Disaster Recovery
MAY 8, 2024
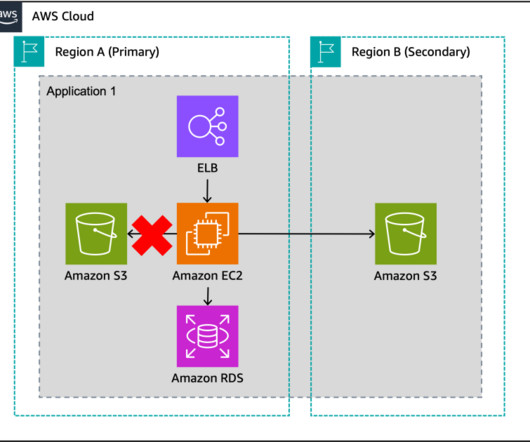
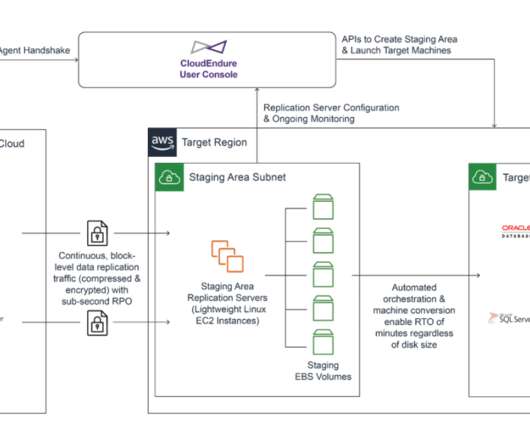
This allows you to build multi-Region applications and leverage a spectrum of approaches from backup and restore to pilot light to active/active to implement your multi-Region architecture. The component-level failover strategy helps you recover from individual component impairments.














Let's personalize your content