Journey to Adopt Cloud-Native Architecture Series: #3 – Improved Resilience and Standardized Observability
AWS Disaster Recovery
APRIL 27, 2021
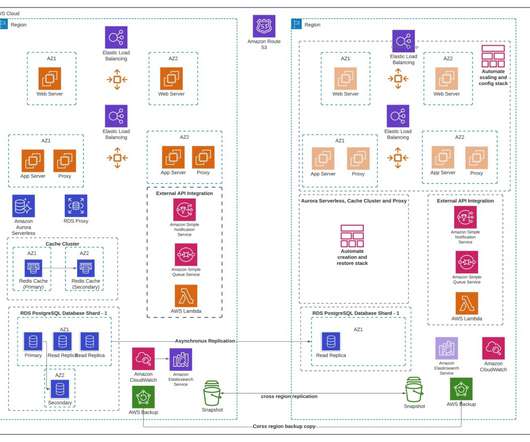
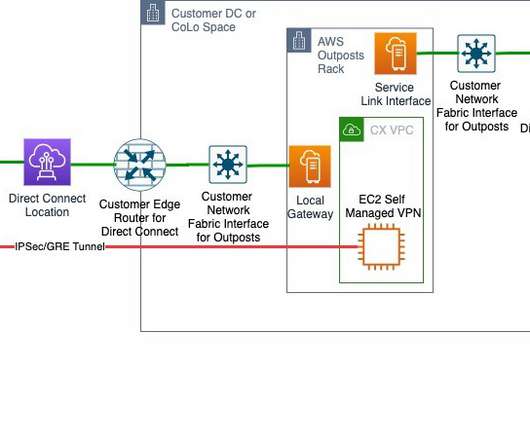
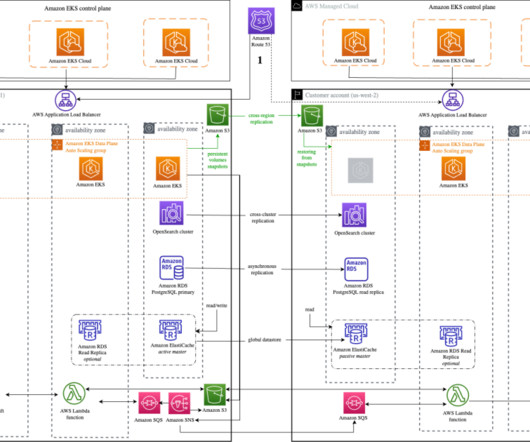
In this blog, we talk about architecture patterns to improve system resiliency, why observability matters, and how to build a holistic observability solution. Earlier, we were able to restore from the backup but wanted to improve availability further. Our analysis also uncovered a gap in security monitoring. Conclusion.









Let's personalize your content