
Preparedness Starts With a Threat and Vulnerability Assessment
Take time to anticipate the full range of potential disruptions and safety risks when business is good, so you can work to mitigate these risks before they upset the balance.

“Safety and security departments have a hard time proving that their activities offer a financial ROI, which can result in reduced budget and trying to do more with less,” explains Sara Pratley, SVP of Global Intelligence at AlertMedia. It’s only natural for businesses to seek to cut costs, but it’s a mistake to do so while blind to the risks the organization faces.
To counter this, every safety department needs a tangible analysis of its unique position in the world to demonstrate what’s required to maintain safety. One of the best ways to do this is with a threat and vulnerability assessment.
What Is a Threat and Vulnerability Assessment?
A threat and vulnerability assessment, also known as a threat and vulnerability risk assessment or TVRA, is a methodology of vulnerability management to protect your organization from any and all possible disruptions. It’s a critical component of all-hazards preparedness. By cross-referencing a deep understanding of your business assets and processes with a comprehensive external threat outlook, any organization can improve its business resilience and appreciate the often-unseen efforts of safety and security teams. Let’s look at each of its constituent parts:
Assets
Assets are anything of value your business owns or can otherwise make use of. This encompasses everything from real estate to human capital to equipment to intellectual property. Ultimately, protecting your business comes down to protecting all assets so that they can contribute their full value to the operation.
Vulnerabilities
A business vulnerability is an asset that is exposed to any kind of threat. Common examples include malfunctioning physical security measures, workers who fall for phishing scams and other cyberattacks, poor network security, insurance liability, and intellectual property infringement.
Threats
Threats represent the endless types of danger that exist in our environment. Anything that has the potential to negatively affect an organization is included in this definition. From viral pandemics to active shooters to severe weather, every adverse event counts as a threat, whether it has the capacity to influence your business directly or not.
Identify your business’ most critical threats with this fill-in-the-blank template.
Pro Tip: Threat intelligence systems make surfacing threats much more reliable.
Risk
Risk is the potential harm inflicted by a threat on one of your vulnerable assets. It includes a wide variety of risks, from security to brand reputation risks.
The intersection of asset vulnerabilities and threats is a good way of looking at organizational risk. It’s important to note that risk is unique from organization to organization. For example, companies on the Japanese coast are more exposed to tsunami risks than those operating in inland central Europe.
How to Perform a Threat Vulnerability Assessment
Analyzing your business and the environment in which it operates is key to performing a successful threat vulnerability assessment. Let’s walk through each step required to do so.
1. Catalog threats

Businesses don’t operate in a vacuum. Both internal and external threats can spell varying degrees of disaster for your critical assets and operations. Before you focus on threat mitigation, you must first know and understand those threats in their entirety.
The best way to do that is with a threat catalog. Identifying and listing every known threat in your area will open new windows for viewing your organization’s preparedness.
Threats can be anything with potential adverse effects. Don’t worry about how these potential risks would impact your business—we’ll get to that later. Remember that threats can be internal (from within the company) and external (from outside the company).
First, gather business leaders and stakeholders to brainstorm a written list of every potential threat in your physical area, within your company, and those not tied to physical locations, such as common computer viruses.
From there, the group should answer the following questions for each potential threat:
- Where does it originate?
- How common is it?
- Has it affected the organization before?
The type and number of threats can seem overwhelming initially, but it can help break them down into categories. Common types of threats that you should consider to get you started are:
Physical security
So many security vulnerabilities are encapsulated in the risk of poor access control to your workplace. Be it active shooters, property theft, converged security threats, or even just a nuisance that disrupts the work environment, they all fall into this category.
Information technology
A popular target among threat actors these days, anything that stems from your computer systems belongs in the IT risk category. This includes the increasingly prevalent threat of cyberattacks like hackers, ransomware, and sensitive data breaches but also encompasses human-based threats like phishing attacks or catastrophic user errors.
Natural
From hurricanes to earthquakes to global pandemics, the natural world has a varied arsenal of threats to your business. Of course, this category is very broad. Depending on the threats in your area, you might want to break it up into sub-categories such as natural disasters and hazardous weather.
Socio-political
Civil unrest, protests, laws, curfews, and more can have a profound impact on a company’s ability to continue operations. As a part of the larger society, your business can’t be completely insulated from those forces.
2. Analyze assets
To understand your business as a complex system, you must first understand its constituent parts. The best way to do so is to create an “asset record.” This record will be an authoritative list of all assets and their key attributes.
Collaborate with department leaders to make sure you don’t miss anything. Those leaders are usually well-versed in how assets under their purview work and fit into the larger business apparatus, so including them from the start will save time and effort. It’s a good idea to organize attributes by categories, such as by the departmental owner and location.
For each item on this list, consider how it fits into your larger business ecosystem. The following questions can help guide your efforts:
- Who is responsible for the asset?
- Who works with it?
- What are its inputs?
- What does it output?
- What other assets/systems rely on this?
- Has it failed/become compromised before?
- If so, how? And how did you recover it?
- Are we aware of any alternative?
Determine vulnerability
Now comes the fun part—with the information you’ve gathered on your assets and known threats, it’s time to combine and assess them together. It’s kind of like theoretical penetration testing.
For each of your assets, think about which threats are actually threatening. For example, a construction company’s cement mixer assets likely won’t be directly impacted by a viral pandemic, but they very well could be damaged by exposure to seasonal hailstorms. This will help you quantify the vulnerability. Some choose to assign numbers (say, 1–5) to indicate vulnerability. You can also just assign them vulnerabilities of low, medium, and high. It doesn’t matter exactly how you do it as long as you sort them by the likelihood of their occurrence.
This is a time-consuming process, but it’s the heart of the threat and vulnerability assessment exercise. By comparing each of your assets with each identified threat, you’ll paint a detailed landscape view of your organization’s vulnerabilities.
Predict impact
After analyzing your assets’ vulnerabilities, you need to predict how those vulnerabilities will impact your business overall. To continue the cement mixer example, if your team seldom uses that piece of equipment, the impact will be relatively low. On the other hand, if your crews rely on them daily, all your construction projects could be delayed until you can find replacements or make repairs, meaning a very high impact.
Just as you did with your vulnerability analysis, categorize these impacts by severity.
3. Synthesize risk level
Once you’ve gathered your vulnerabilities and impacts, it’s time to plot them on a threat matrix, much like you do with a business threat assessment. A threat matrix is a grid on which you can visualize both the likelihood and severity of any given vulnerability. The X-axis represents likelihood, while the Y-axis represents severity.
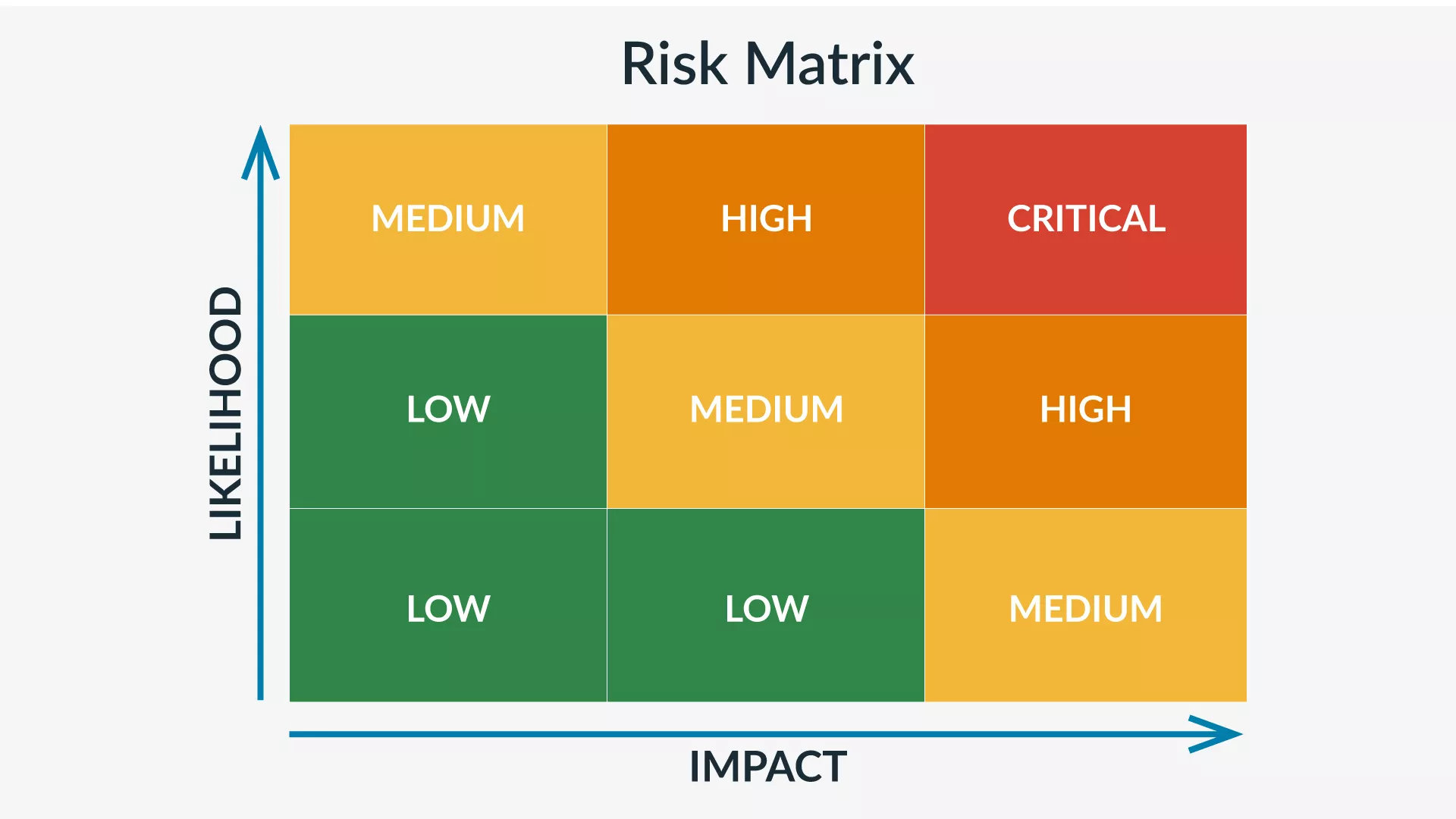
You’re then left with a visual representation of the risk level of each asset’s vulnerability. Vulnerabilities with a high likelihood and high impact are high risk, those with low likelihood and impact are low risk, and then there are those somewhere in the middle.
4. Devise solutions
When you’ve determined the risk levels, you can focus on threat remediation. For those with very low risk and impact, you might choose to accept that low level of risk if the effort to mitigate is greater than the benefit of doing so. Conversely, those with high impact and high likelihood would be priorities for your team to mitigate.
The countermeasures to any of these vulnerabilities are as varied as the risks themselves, so work with the team that helped with the asset analysis and threat catalog to determine the most effective responses (for example, the construction company should keep their mixers under a roof when the weather forecasts hail). With the risk levels in mind, your brain trust will have a much easier time preempting and intercepting any business disruptions and undertaking successful risk management.
(In)vulnerable
When business is good, it’s easy to take stability for granted. But this is precisely the time to anticipate the gamut of disruptions and safety risks so you can work to mitigate them before they upset the balance.
Whether it’s hurricanes, cyber threats, or any other threat, your assessment gives you the opportunity to close security gaps, plan for emergencies, and ultimately avoid harm to your people and operations. When you use our threat assessment template, you won’t feel like starting from scratch with this high-stakes task.

![4 Steps to Conduct a Business Threat Assessment [+ Template]](https://www.alertmedia.com/wp-content/uploads/2022/07/Blog-Image-Business-Threat-Assessment-V1.jpg)


