Risk Management Process- Part 3a: Risk Assessment and Risk Identification
In the previous post of this risk management series, we covered the business impact analysis (BIA), which is a crucial step in understanding the impact of potential disruptions to critical business processes. Now, we move on to the next critical step in the process: risk assessment, and its first stage, risk identification.
What Is Risk Assessment?
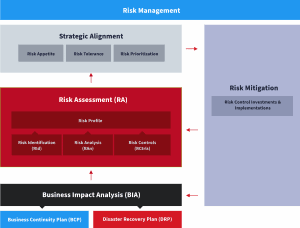
Risk assessment is a key component of the risk management process that identifies and evaluates all potential risks faced by an organization. This includes risks to strategy, finances, compliance, governance, and operations. Within the context of business continuity, risk assessment focuses on operational risks that may result in business disruption.
It identifies threats and vulnerabilities, potential areas of impact, and the likelihood of disruptive events. The risk assessment process also documents existing strategies and measures to mitigate risk.
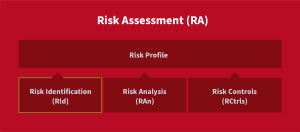
In the third part of this series, we’re going to take a closer look at the four elements of risk assessment: risk identification, risk analysis, risk control, and risk map.
What Is Risk Identification?
Risk identification is the first step of risk assessment. It involves identifying all potential risks that an organization may face in its operations and its assets. It is critical to consider all possible risks, even those that seem unlikely, as they can have significant consequences if left unaddressed.
The objective of this step is to leave no stone unturned and to uncover all conceivable hazards, however minor or remote. Each risk identified provides an opportunity to develop strategies to mitigate its impact and ensure the organization’s continued stability.
The Importance of Risk Identification
The aim of risk identification is to create a comprehensive inventory of all possible hazards that could potentially disrupt an organization’s operations and assets. By meticulously identifying every potential risk, an organization gains the necessary insight to prioritize risks, distinguishing which pose the most pressing threats and require immediate attention.
With this understanding, an organization can develop effective strategies to mitigate each risk, safeguarding its operations and protecting its assets from harm.
What Is in a Risk Identification Report?
A risk identification report is a comprehensive list of all the potential risks that could threaten the success of a project, enterprise, or business unit.
A well-crafted report includes a detailed account of each identified risk, providing critical information on its potential impact and the likelihood of it occurring. This data is crucial for decision-makers, as it allows them to prioritize risks and develop targeted strategies to mitigate them.
Risks by Category
Categorizing risks makes it easier to prioritize them. For example, risks can be classified as financial, operational, strategic, reputational, or legal.
Notion of Impact
It’s also crucial to understand who and what will be affected by each risk. This can include systems, applications, business processes and/or functions, parts of the infrastructure, employees (including different types of employees and where they’re located), customers, partners, and the local community.
Risk Register
Once the risks have been identified, they need to be documented in a risk register. A risk register is a tool that helps organizations document and manage their threats.
The risk register should include:
- All identified risks associated with a project, enterprise, or business unit.
- The risk category, which helps prioritize the risk.
- The likelihood of each risk becoming a threat or event. This may also be known as a risk rating (high, medium, or low chance).
- The potential consequences of each risk event occurring.
- The costs to mitigate each risk. This information can help in budgeting and prioritizing resources.
- The specific steps required for appropriate risk mitigation. These steps aid organizations in developing effective mitigation strategies.
- The name or title of the risk owner, the person responsible for managing each specific risk.
The risk register is a living document that should be regularly reviewed and updated to reflect changes in an organization’s risk landscape. By maintaining an up-to-date risk register, organizations can better manage their identified risks and reduce the impact of disruptive events.
Methods of Identifying Risks
There are several methods for identifying risks, including:
- Interviews—Conducting interviews with key stakeholders is a vital component of the risk identification process. By tapping into the expertise of those who are intimately familiar with the organization’s operations and infrastructure, interviewers can uncover potential risks and vulnerabilities that may not have been immediately apparent.
- Surveys—When it comes to gathering information on potential risks, surveys can be an invaluable tool. By soliciting input from a large and diverse group of individuals, organizations can gain a broader understanding of the risks they face.
- Analysis of Internal and External Data—To conduct a thorough and effective risk assessment, it’s essential to analyze both internal and external data sources. By mining internal data, such as financial reports, incident reports, and performance metrics, an organization can gain valuable insights into its own operations and identify areas where vulnerabilities may exist. However, internal data is only one piece of the puzzle. To truly understand the risks facing an organization, it’s necessary to examine external data sources as well. This could include keeping a finger on the pulse of market trends, monitoring regulatory changes, or assessing geopolitical risks that could impact the organization’s operations.
Once the organization has gathered a comprehensive inventory of the risks it faces (threats and vulnerabilities), it’s time to assess them to understand their criticality to the business. This is what we are going to explore next.