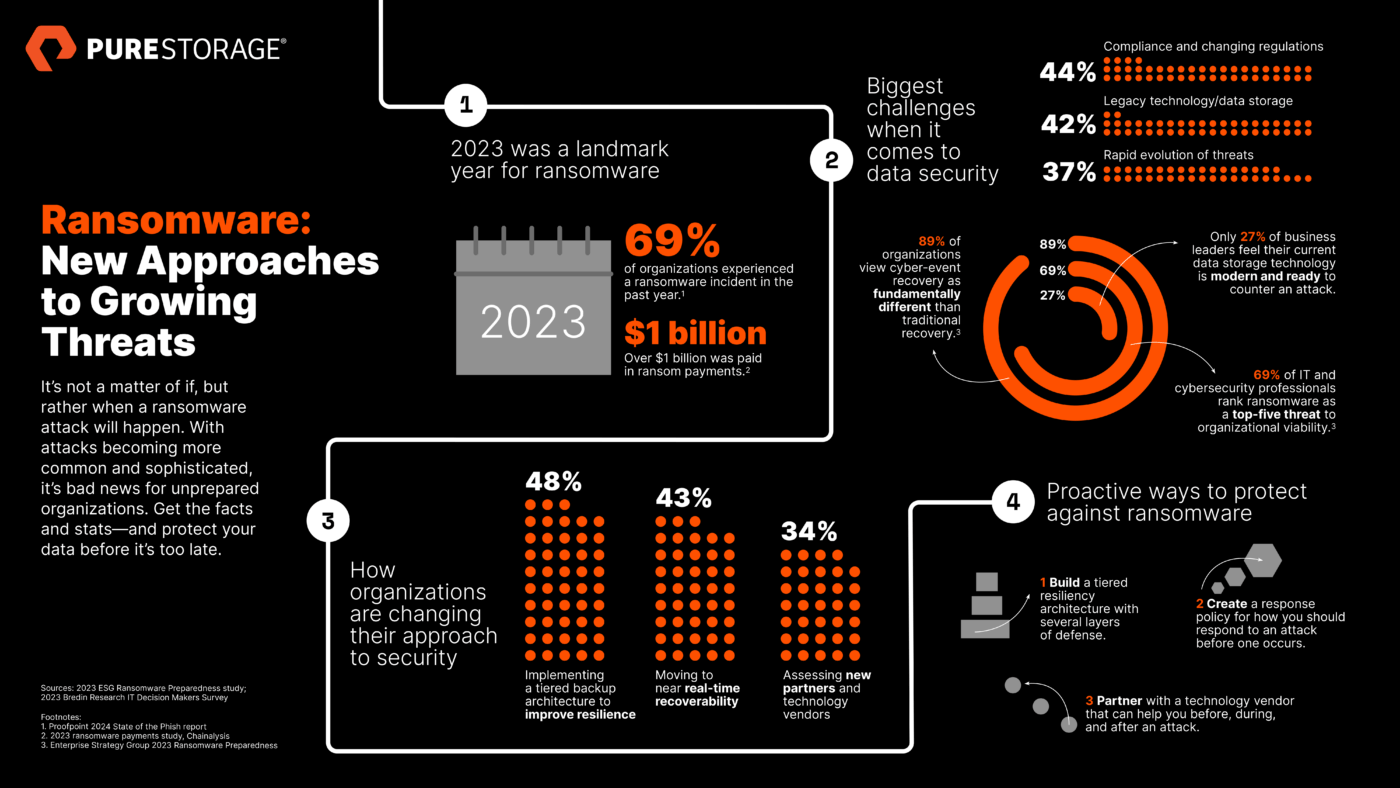
Cybercriminals are becoming increasingly bold these days, evolving their tactics and attacks as fast as we can evolve our defenses. What if, in the ongoing war against cybercrime, you could get intel on what they’re up to straight from a former hacker? Now you can.
I worked with former hacker turned internationally-renowned cybersecurity expert, Hector Xavier Monsegur to create a comprehensive ebook designed to help you create the best defensive plan possible.

What are the most important things to know about ransomware?
As a former black hat-turned white hat hacker, Hector has his thumb on the pulse of ransomware today. What he thinks you should keep top of mind includes:
- Ransomware is growing more sophisticated. From state-sponsored hacker groups and cryptocurrencies to off-the-shelf tools and AI, Hector says hacking isn’t what it used to be. These capabilities enable skilled (and more increasingly unskilled) offensive actors to scale and rent out their capabilities, like mercenaries.
- Encryption-less attacks are challenging cybersecurity professionals. In these ransom attacks, attackers bypass encryption to directly target and compromise essential systems and data, with tools such as wiperware. Now is the time to understand their techniques leading up to an attack and develop effective mitigation strategies.
- Cyber insurance coverage could encourage more attacks. Attackers have even been known to research how much insurance a target company has and then ask their victim to pay that amount. In fact, enterprises with larger budgets for cyber insurance could be more lucrative targets for bad actors.
- Good security hygiene is still sorely lacking in many organizations. Too many IT teams are failing to address obvious security gaps in backup and recovery infrastructure. Those that don’t practice good security hygiene, such as password authentication, identity management, backup policies, and incident management, make life easy for attackers.
How does a former hacker suggest companies fight ransomware?
Today, Hector is an offensive security-focused “Red Team” researcher. This means he works with organizations to emulate how cybercriminals might carry out an attack to help defense-focused “Blue Teams” understand where their risks and gaps are.
He says there’s a 3-pillar to approach cybersecurity: before, during, and after an attack. With this approach you can design a top-to-bottom response policy that guides you through each phase:
- Preventative measures before an attack. Better visibility into your data, fast security log analytics, and a tiered resiliency architecture are the sharpest tools in your box. Hector says a smaller attack surface area is easier to protect, and you have to “make life harder” for them with tougher defenses.
- Swift mitigation and response plans during an attack. Hector warns, “Just because the network is quiet doesn’t mean an attacker isn’t lurking on it.” Catching anomalies earlier can stop or slow the spread. Hector also says hackers are counting on chaos when an attack is detected, and a panic response. Having a response handbook ready will keep you prepared and focused.
- Fast recovery tools after an attack. Many organizations forget the fact that affected equipment technically becomes evidence after an attack—and can’t be used to get back online. Among other things, hands-on recovery support from a Ransomware Recovery SLA is your best bet.
This just scratches the surface. Get inside the mind of a former hacker and learn all the things hackers don’t want you to know with the A Hacker’s Guide to Ransomware Mitigation and Recovery ebook.
With the rise in high-dollar, high-tech ransomware attacks, this e-book is a resource you can’t afford not to have. To learn exactly what you should be doing to prevent and recover from an attack and how Pure Storage solutions can help, download the e-book today.
It’s time to outsmart ransomware attackers at their own game!
Download “A Hacker’s Guide to Ransomware Mitigation and Recovery” E-Book