This blog on static and dynamic code scanning in DevSecOps was co-authored by Dr. Ratinder Paul Singh Ahuja, CTO for Security and Networking, and Rajan Yadav, Director of Engineering, CNBU (Portworx), Pure Storage. Dr. Ahuja is a renowned name in the field of security and networking.
In part two of our series exploring our “6-Point Plan,” we delved into the second facet of a comprehensive DevSecOps strategy: threat modeling. We explored the nuances of threat modeling and the intricacies of STRIDE analysis. We dissected prevalent cyber threats, elucidated best practices, and underscored the indispensable nature of threat modeling in the realm of cybersecurity.
In part three, we’ll pivot our focus toward the third element of our strategic framework—static and dynamic code scanning. This will be an in-depth exploration of this critical aspect. And, we’ll also scrutinize the merits and demerits of the plethora of scanning tools available in the security landscape and how you can build a more comprehensive approach toward static and dynamic code scanning.
What Is Code Scanning?
Code scanning is the automated process of analyzing source code for potential security vulnerabilities, coding errors, and compliance violations. It’s an essential part of the DevSecOps lifecycle that aims to integrate security into the software development process from the start
Code scanning can be performed at various stages of the development lifecycle—from early prototyping to production deployment. Static application security testing (SAST) is the most common type of code scanning. SAST analyzes source code for potential vulnerabilities without executing it. Other types of code scanning include dynamic application security testing (DAST), which executes code and analyzes its behavior for vulnerabilities, and software composition analysis (SCA), which analyzes third-party components for known vulnerabilities.
MITRE Common Weakness Enumeration
The Common Weakness Enumeration (CWE) is a category system for hardware and software weaknesses and vulnerabilities that’s operated by the MITRE Corporation with support from US-CERT and the National Cybersecurity Division of the U.S. Department of Homeland Security. CWE is a community project with the goal of understanding flaws in hardware and software and creating tools that can be used to identify, fix, and prevent those flows.
The MITRE CWE Top 25 Most Dangerous Software Weaknesses list is calculated by analyzing public vulnerability data in the National Vulnerability Database (NVD) for root cause mappings to CWE weaknesses for the previous two calendar years. The CWE Top 25 also incorporates updated weakness data for recent CVE records in the data set that are part of CISA’s Known Exploited Vulnerabilities Catalog (KEV).
The 2023 MITRE CWE Top 25 list includes:
| # | CWE ID | Name | Impact and Mitigation Recommendations |
|
|
CWE-787 | Out-of-bounds Write | Impact: Arbitrary code execution or crash. Mitigation: Implement bounds checking. |
| 2. | CWE-79 | Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’) | Impact: Hijack user sessions, deface websites. Mitigation: Sanitize input, use CSP. |
| 3. | CWE-89 | Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’) | Impact: Unauthorized database access. Mitigation: Use prepared statements, parameterized queries. |
| 4. | CWE-416 | Use After Free | Impact: Arbitrary code execution. Mitigation: Ensure proper memory management and deallocation. |
| 5 | CWE-78 | Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’) | Impact: Execution of arbitrary commands. Mitigation: Sanitize inputs, use secure APIs. |
| 6. | CWE-20 | Improper Input Validation | Impact: Various, based on exploitation context. Mitigation: Validate all inputs. |
| 7. | CWE-125 | Out-of-bounds Read | Impact: Information disclosure, crash. Mitigation: Implement bounds checking. |
| 8. | CWE-22 | Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’) | Impact: Unauthorized file access. Mitigation: Sanitize file paths, enforce access controls. |
| 9. | CWE-352 | Cross-Site Request Forgery (CSRF) | Impact: Unauthorized actions on behalf of users. Mitigation: Use anti-CSRF tokens. |
| 10. | CWE-434 | Unrestricted Upload of File with Dangerous Type | Impact: System compromise, malware upload. Mitigation: Restrict file types, scan for malware. |
| 11. | CWE-862 | Missing Authorization | Impact: Unauthorized access to functionality. Mitigation: Implement proper authorization checks. |
| 12. | CWE-476 | NULL Pointer Dereference | Impact: Application crash, potential code execution. Mitigation: Validate pointers before use. |
| 13. | CWE-287 | Improper Authentication | Impact: Unauthorized access. Mitigation: Strengthen authentication mechanisms. |
| 14. | CWE-190 | Integer Overflow or Wraparound | Impact: Memory corruption, arbitrary code execution. Mitigation: Validate integer calculations. |
| 15. | CWE-502 | Deserialization of Untrusted Data | Impact: Arbitrary code execution. Mitigation: Avoid deserializing data from untrusted sources. |
| 16. | CWE-77 | Improper Neutralization of Special Elements used in a Command (‘Command Injection’) | Impact: Similar to OS command injection. Mitigation: Input validation, use safe APIs. |
| 17. | CWE-119 | Improper Restriction of Operations within the Bounds of a Memory Buffer | Impact: Buffer overflows, arbitrary code execution. Mitigation: Use safe library functions, bounds checking. |
| 18. | CWE-798 | Use of Hard-coded Credentials | Impact: Unauthorized access. Mitigation: Use secure storage for credentials, implement dynamic secrets. |
| 19. | CWE-918 | Server-Side Request Forgery (SSRF) | Impact: Unauthorized internal network access. Mitigation: Validate and sanitize URLs, restrict URL schemes. |
| 20. | CWE-306 | Missing Authentication for Critical Function | Impact: Unauthorized use of critical functions. Mitigation: Ensure authentication for all sensitive functions. |
| 21. | CWE-362 | Concurrent Execution using Shared Resource with Improper Synchronization (‘Race Condition’) | Impact: Data corruption, security bypass. Mitigation: Implement proper synchronization mechanisms. |
| 22. | CWE-269 | Improper Privilege Management | Impact: Escalation of privileges. Mitigation: Adhere to the principle of least privilege. |
| 23. | CWE-94 | Improper Control of Generation of Code (‘Code Injection’) | Impact: Arbitrary code execution. Mitigation: Sanitize inputs, use safe APIs. |
| 24 | CWE-863 | Incorrect Authorization | Impact: Bypassing of authorization checks. Mitigation: Implement robust authorization checks and audits. |
| 25. | CWE-276 | Incorrect Default Permissions | Impact: Unauthorized access, privilege escalation. Mitigation: Set secure defaults, review permissions. |
The weaknesses on this list are particularly dangerous because they can be easy to find and exploit. They can also open up opportunities for adversaries to take over a system, steal data, and prevent an application from working.
The Importance of Code Scanning
Code scanning is the process of examining code to identify bugs, errors, and security flaws. It plays an important role in the DevSecOps lifecycle for a variety of reasons, helping to:
- Identify and fix security vulnerabilities early in the development process. This can help to reduce the cost and complexity of fixing vulnerabilities later on. It can also help to prevent vulnerabilities from being introduced into production software.
- Improve the overall quality of code. Code scanning can also identify coding errors and compliance violations, which can help to improve the overall quality of code.
- Reduce the risk of security breaches. By identifying and fixing security vulnerabilities early on, code scanning can help to reduce the risk of security breaches and data loss.
Specific examples of how code scanning can be used in the DevSecOps lifecycle include:
- A developer can use a code scanner to check their code for vulnerabilities before they commit it to the code repository.
- A security team can use code scanners to scan the codebase on a regular basis for new vulnerabilities.
- A continuous integration (CI) pipeline can include code scanning as a step to ensure that code is secure before it is deployed to production.
Static vs. Dynamic Code Scanning
Static and dynamic code scanning are two complementary techniques for identifying security vulnerabilities and other defects in software. Static code scanning analyzes source code without executing it and can be used to identify a wide range of issues, including:
- Coding errors
- Security vulnerabilities
- Compliance violations
- Performance problems
- Design issues
Dynamic code scanning analyzes running code. It’s typically used to identify vulnerabilities that are only exploitable when the code is running, such as:
- Buffer overflows
- Race conditions
- Injection vulnerabilities
- Cross-site scripting (XSS) vulnerabilities
Static code scanning is best used early in the software development lifecycle, during the coding and design phases. It can be used to identify and fix issues before they are introduced into the codebase, which can save time and money in the long run. Static code scanning can also be used to:
- Enforce coding standards
- Improve the overall quality of code
- Reduce the risk of security breaches
Dynamic code scanning is best used later in the software development lifecycle, during the testing and deployment phases. It can be used to identify vulnerabilities that may not be detected by static code scanning, such as vulnerabilities that are only exploitable when the code is running in a specific environment. Dynamic code scanning can also be used to:
- Test the security of running applications
- Validate the results of static code scanning
- Identify vulnerabilities in third-party software
The Rise of Open Source and Its Security Implications
The rise of open source has revolutionized the software landscape, offering a wide range of benefits alongside nuanced security implications. Embracing open source code fosters innovation, collaboration, and cost-efficiency. Developers leverage a vast community’s collective expertise, accelerating development and customization. Moreover, transparency enables scrutiny, enhancing code quality and reliability.
However, this openness presents challenges. While advantageous, reliance on open source dependencies can introduce potential risks. Developers may unwittingly incorporate outdated or unpatched libraries, leaving systems vulnerable to exploits. Real-world breaches underscore this risk. Notable instances include the Equifax breach in 2017, where attackers exploited an unpatched Apache Struts vulnerability, affecting millions. Thus, while open source offers unparalleled advantages, diligent management and constant vigilance are imperative to navigate its complex security landscape.
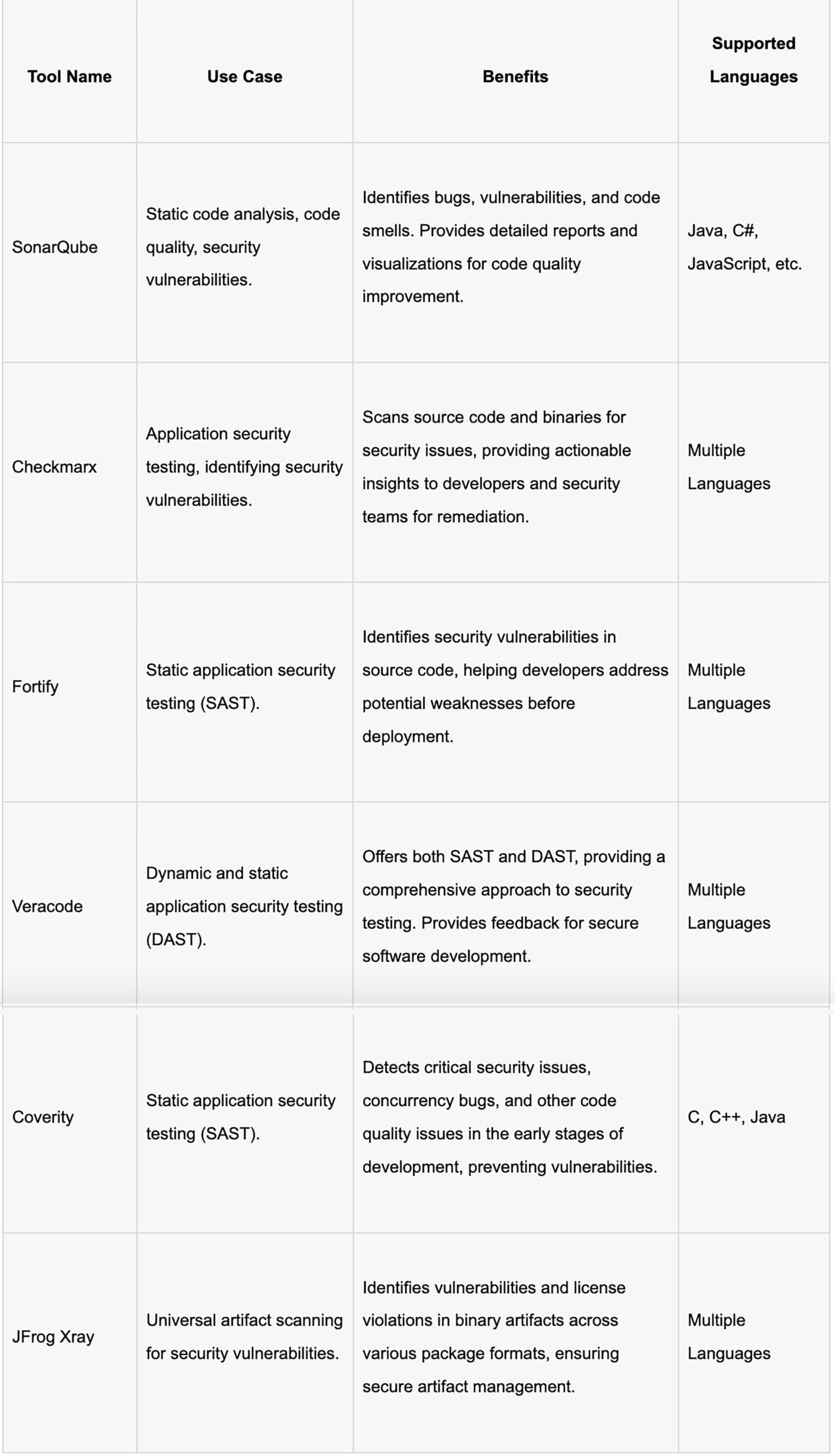
Tool Spotlight
There are a variety of tools available for dynamic and static code scanning. The following table, though not comprehensive, lists some of the common tools that can be used in DevSeCops pipelines for static and dynamic code scanning.
Best Practices for Integrating Scanning Tools in DevSecOps
There are valuable learnings from our adoption of these tools and making them work at scale. First, early integration in the CI/CD pipeline is essential. In the true spirit of left-shifting security, the CI pipelines should be able to give feedback on code quality from a security standpoint as the developer is writing code. For this to happen, the integrated development environments (IDEs) used by developers must be integrated with code scanning tools that the company/team has adopted.
Automating vulnerability remediation is also necessary. The integrated scan with IDEs should provide recommendations on fixes. You’ll then want verification if vulnerabilities have been remediated. Services like GitHub Advanced Security can then be leveraged to verify if the developer has addressed all the identified security issues in the code when a PR is submitted to the CI pipelines.
It’s expected that the tool of choice has continuous monitoring and updating of vulnerability databases. Ensuring developer training and awareness is essential for proactive vulnerability management.
Proprietary Code: Why It’s Not Immune
There are common misconceptions about proprietary code security. For example, one technical misconception is that proprietary code doesn’t require regular vulnerability scanning because it’s not widely used or targeted like popular open source software. This overlooks a critical fact: The complexity and uniqueness of proprietary software can often lead to specific, hard-to-detect vulnerabilities.
For instance, proprietary software may use unique algorithms or data structures that haven’t been as thoroughly vetted for security flaws as their open source counterparts. This lack of external review can leave hidden vulnerabilities, such as buffer overflows or SQL injection points, which are only discovered when they are exploited. The reality is there is a need for rigorous scanning and testing, even for in-house developed code.
In the realm of proprietary code, one technical challenge is the integration of third-party libraries or APIs that may not be fully scanned for vulnerabilities. Developers often use these components for efficiency, but they can introduce security risks if not properly vetted. A technical example is the use of custom encryption methods in proprietary software. While in-house encryption algorithms might seem secure, they often lack the rigorous testing that standard encryption methods undergo. This can lead to vulnerabilities in cryptographic implementations, making the software susceptible to attacks like side-channel attacks or cryptographic bypasses. Rigorous scanning and penetration testing are crucial to uncover these technical vulnerabilities, ensuring the integrity and security of the proprietary software.
There have been several high-profile incidents where vulnerabilities in proprietary code led to significant security breaches. For example, the Equifax breach in 2017, one of the largest data breaches in history, was due to an unpatched vulnerability in proprietary web application software. Another instance is the SolarWinds hack, a sophisticated cyber-espionage campaign discovered in 2020, which was perpetrated through malicious code inserted into the company’s proprietary software updates. These cases highlight the critical need for stringent security measures in proprietary code to prevent such devastating incidents.
Addressing False Positives and False Negatives
False positives in code scanning refer to instances where the scanning tools incorrectly identify a piece of code as vulnerable or problematic when it is not. This can lead to unnecessary alarm and waste of developer resources. To mitigate this, organizations can implement machine learning-based algorithms that learn from past scanning results to improve accuracy. For example, tools like SonarQube use sophisticated pattern recognition to distinguish between true and false positives. Additionally, integrating human reviews and cross-referencing with vulnerability databases can help filter out false positives. Regularly updating the scanning tools’ rulesets and algorithms based on real-world feedback also ensures that the tools stay relevant and accurate.
In contrast, false negatives occur when scanning tools fail to detect actual vulnerabilities, which is a significant risk as it leaves systems exposed to potential breaches. To address this, organizations should adopt a layered scanning approach, combining multiple tools like static application security testing (SAST), dynamic application security testing (DAST), and interactive application security testing (IAST) to cover different aspects and stages of the development lifecycle. This comprehensive approach increases the likelihood of detecting vulnerabilities that might be missed by a single tool. Additionally, incorporating manual penetration testing into the security strategy helps uncover vulnerabilities that automated tools might overlook. Regularly updating and configuring the tools to keep up with emerging threats and changing codebase structures is crucial to minimize false negatives.
Ensuring Timely Patching without Disrupting Development Workflows
Timely patching of vulnerabilities is crucial, but it must be balanced with maintaining efficient development workflows. A technical approach to achieve this is the implementation of automated scan and patch management frameworks. These frameworks can be integrated into continuous integration/continuous deployment (CI/CD) pipelines.
For instance, using tools like Dependabot or Snyk, which automatically detect and suggest fixes for vulnerabilities in dependencies, greatly reduces the effort required by developers. These tools can be configured to automatically create pull requests for patching, allowing developers to review and merge them with minimal disruption.This integration ensures that security updates are handled proactively, without adding significant overhead to the development process. At Pure Storage, we leverage multiple scanning tools and have built a proprietary algorithm to reduce developer toil by filtering out unfixable vulnerabilities (vulnerabilities that don’t have fixes available). This allows developers to focus only on fixable vulnerabilities.
Balancing between Security and Development Speed
Achieving a harmonious balance between security and development speed hinges on the seamless integration of security protocols within the development cycle. This integration is a cornerstone of the DevSecOps approach, ensuring that security considerations are embedded at each phase of the software development process. Modern tools like GitHub Copilot, which leverages AI to assist in code writing, can be harnessed to provide real-time insights and suggestions, including security-related advice, directly within the integrated development environment (IDE).
This immediate feedback loop enables developers to concurrently address potential security issues while writing code, thereby reducing the likelihood of extensive revisions later on. This approach not only preserves the pace of development but also embeds security as a fundamental aspect of the coding process. Moreover, the utilization of advanced interactive application security testing (IAST) tools further augments this strategy by merging the strengths of both static and dynamic analyses, delivering prompt and accurate security feedback as the development unfolds.
The Rise of Vulnerability Middleware
Vulnerability management middleware is emerging as a solution to streamline the handling of security vulnerabilities in complex software systems. This middleware acts as an intermediary layer that aggregates, analyzes, and prioritizes vulnerabilities from various scanning tools and sources. By providing a centralized view and actionable insights, it helps organizations to more effectively manage their vulnerability landscape.
An example is the use of middleware platforms that leverage machine learning algorithms to prioritize vulnerabilities based on their potential impact and the likelihood of exploitation. This approach ensures that the most critical vulnerabilities are addressed first, enhancing the overall security posture without overwhelming the development team with a high volume of alerts. The middleware not only simplifies the process but also ensures a more accurate and efficient vulnerability management process, reducing the noise of false positives and focusing on truly impactful security issues.
The Significance of Integrating Static and Dynamic Code Scanning within the DevSecOps Framework Can’t Be Overstated
The integration is not merely an enhancement; it’s an essential strategy for ensuring the security and reliability of software products in a digital world where threats are increasingly sophisticated and pervasive. The adoption of both static and dynamic code scanning methods provides a comprehensive defense mechanism, proactively identifying potential vulnerabilities and ensuring that they are addressed before they can be exploited.
Organizations must recognize that the journey toward robust software security is continuous and demands a proactive approach. Embracing a culture where security is not an afterthought, but rather a fundamental aspect of the development process, is critical. This approach requires a paradigm shift from reactive to proactive vulnerability management—a shift that can significantly reduce the risk of security breaches and enhance the overall trustworthiness of software systems.
As we look to the future, the role of static and dynamic code scanning in DevSecOps will only grow in importance. It’s incumbent upon organizations to not only adopt these practices but also to continuously evolve them, staying ahead of emerging threats and fostering an environment of relentless improvement in software security. The path forward is clear. A steadfast commitment to proactive security measures, underpinned by advanced code scanning techniques, is essential for the creation of secure, resilient, and trustworthy software in the modern digital era.
Stay tuned for the next installment in our DevSecOps blog series where we’ll dive into the critical realm of configuration hardening. We’ll focus on the essential strategies for securing operating systems, build environments, secret management, and container images—a cornerstone in safeguarding your CI/CD infrastructure.
Explore More
Do you want to delve deeper? The following resources can help you further your understanding and learning into this vital field:
- OWASP Foundation: A rich resource for understanding web application security, including guidelines on static and dynamic code analysis.
- SANS Institute: Offers a wealth of knowledge on integrating security into DevOps practices, with a focus on code scanning methodologies.
- GitHub Security Lab: Provides insights and tools for code scanning and vulnerability management, particularly in the context of GitHub repositories.
- Docker Blog: Provides insights on container security, including the hardening of container images and environments.
We Want to Hear from You
We invite you to share your insights and experiences with the tools we’ve discussed. Your stories are a valuable resource for others within our community, and your thoughts and queries are vital to us. Please feel free to provide feedback or ask questions at rahuja@purestorage.com.
![]()