ISC East Session Preview: Securing IIoT Using Zero Trust — The Future of IIoT Cybersecurity

ISC East 2022 is coming up Nov. 15-17 in New York City, and the Security Industry Association (SIA) and ISC East recently revealed full conference details for the SIA Education@ISC East program, including keynote presentations from top luminaries and over 30 sessions from top industry expert speakers on the most current business trends, technologies and industry developments.
Among the robust lineup of conference sessions is the presentation Securing IIoT Using Zero Trust – The Future of IIoT Cybersecurity. In this session, i-PRO Americas’ Will Knehr will explore what zero trust is, why organizations like the U.S. Department of Defense embrace the zero trust model and how it can be applied to industrial Internet of Things devices. In this blog, Knehr provides expert insights on this critical topic and gives a sneak peek of what to expect during this session. Join us Thursday, Nov. 17, at 2:00 p.m. to learn more!

IoT is the Internet of Things, and it is typically defined as small computing devices, sensors or software that communicate and exchange data over the internet. Still confused? No sweat, you interact with these devices every day and maybe don’t even realize it. These are devices like smart refrigerators, vacuums, dryers, thermostats, home security systems, wearable fitness and wellness tracking accessories, light switches and even health care devices like pacemakers. Unfortunately, most of these devices were not made with security in mind – they were just made to function and provide convenience to the consumer. Industrial Internet of Things (IIoT) is just like IoT but developed for an industrial market. IIoT includes devices used in manufacturing, heating and cooling of commercial facilities, smart fire control systems, commercial security systems and smart farm devices. These devices automate a lot of commercial processes which increase efficiency and often help to reduce costs, but they have also introduced a new set of vulnerabilities to organizations. Now that we’ve defined IoT and IIoT, let’s discuss some of the issues with securing these devices.
Most modern-day network architectures work a lot like airports. When you enter an airport, you go through a security check showing your ID and a boarding pass, but once you are inside, you can roam freely and check out all the shops, terminals and gates. There is no one stopping you from exploring. Networks are similar. Once you provide your username and password (and maybe some additional factors for authentication), you can poke around and explore. Roaming around freely on the network is something that hackers rely on to look for vulnerable devices, information to steal or ways to escalate their privileges.
So how does zero trust help us out with our roaming problem? Let’s go back to our airport example. Imagine that once you made it through airport security you could only access the terminal, gate and plane that you are authorized to use and are no longer allowed to roam the entire airport checking out other gates, terminals and shops. This fictitious airport scenario is a key idea behind zero trust – the person going to the airport is only allowed to access the airport resources they need to go to their destination and nothing else. In a zero trust network, when someone wants to use a network resource (email, web server, printer or anything else on the network) they are only given access to that resource and nothing else. Access to every resource must be authenticated and approved.
The beauty of zero trust is that not only will it only give access to a specific resource, but it also does something called context analysis. Context analysis is my favorite part of zero trust because it goes so much further than traditional authentication. When someone tries to access a network resource, context analysis looks at the user permissions and privileges; authenticates the user; looks at the device the user is using to access the network and sees if the device belongs on the network, if the device is updated and patched and if it has antivirus and other required software; and checks to see if the policies on the device are correct. Zero trust does a deep analysis of the user, the device and the resource they are trying to access, which makes zero trust much more secure than traditional security architectures. For an example, check out Figure 1 here.
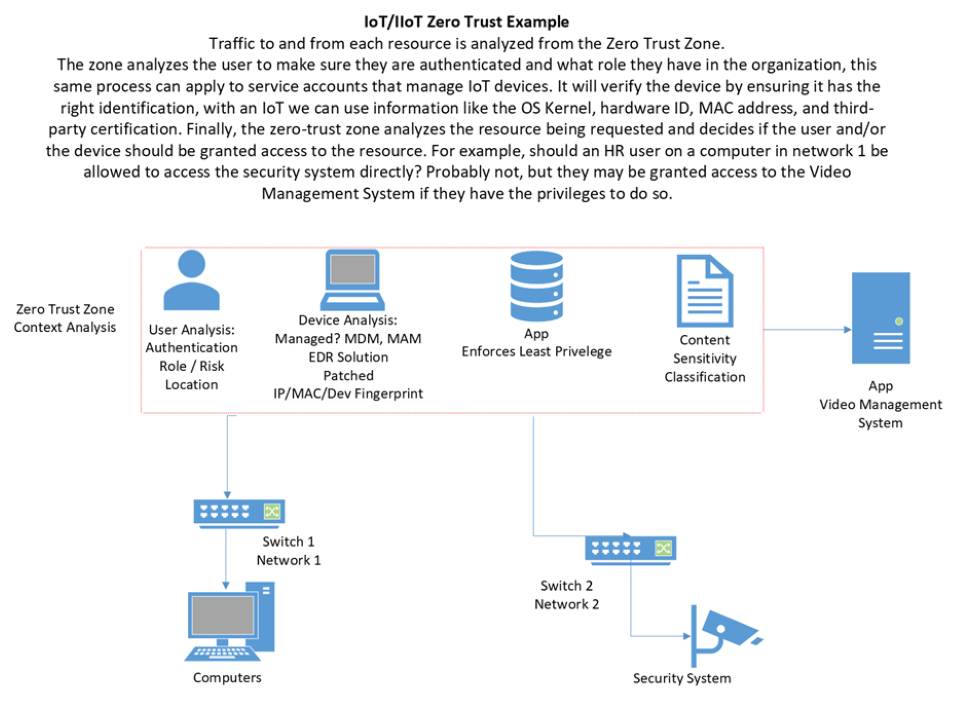
We’ve discussed how zero trust can be used when a user is trying to access a resource, but how does it apply to devices like security cameras, access control systems or IoT/IIoT devices? By using the same principles described above. Let’s use a security camera as an example. Currently, most security cameras use passwords to authenticate to the network, and if you have a good product, they will use a signed certificate as well for encryption. Mix that with a little 802.1x and network segmentation, and you’ve got almost the full extent of IoT/IIoT protection. But at the end of the day, there isn’t much standing between a malicious actor that has gained access to the network and a security camera. To explore this idea, let’s look at the same compromise through two different lenses:
- Scenario 1 — A traditional network computer is compromised by a hacker. The hacker conducts a network scan, discovers the camera on the network and then decides to launch an attack against the camera. The chances that the attacker is successful in compromising the camera, in this case, are very high, especially since the hard part of this attack has already been done, gaining access to the network.
- Scenario 2 — A zero trust network computer is compromised by a hacker. The hacker attempts to access the camera, but the zero trust boundary recognizes that the compromised computer has no business communicating with the camera and blocks the request. The network has detected that the context of the request is abnormal, and the attack was not successful.
Zero trust has so many more implications for IoT/IIoT. Traffic going to the devices can be monitored for context like in the previous scenario, but it can also be used to authenticate the IoT/IIoT device itself. Every device has unique features like a media access control (MAC) address, operating system kernel and hardware ID that can be used to make sure that the device is supposed to be on the network and that it is behaving properly. This helps prevent attackers from using IoT/IIoT devices as attack vectors into the network.
OK, so zero trust is super cool and secure, but you may be wondering, “Why should I truly care and how will this affect me?” Well, the federal government has bought hook, line and sinker into zero trust, with the Biden administration issuing an executive order stating that the federal government must begin working on zero trust integration immediately. Maybe you don’t work on federal contracts, but the last few years have proven that where the federal market goes, state and local governments and education will follow. If zero trust isn’t on your radar now, you’ll be left behind in the next few years. I look forward to exploring this topic further with you at ISC East!
You can access the full SIA Education@ISC conference program for only $75 by registering for a SIA Education@ISC 2-Day Pass here. And don’t forget to use SIA’s free registration link to sign up for the ISC East trade show.
The views and opinions expressed in guest posts and/or profiles are those of the authors or sources and do not necessarily reflect the official policy or position of the Security Industry Association (SIA).
